110m+
users worldwide
400k+
business customers
ESET Endpoint Security for Windows
Multilayered approach balances performance, detection and false positives. Enables organizations to:

Protect against ransomware

Block targeted attacks

Prevent data breaches

Stop fileless attacks

Detect advanced persistent threats
Remote network management
ESET Security Management Center manages endpoint products, including ESET Endpoint Antivirus for Linux, from a single pane of glass and can be installed on Windows or Linux. As an alternative to on-premise server installation, customers with up to 250 seats can opt for ESET Cloud Administrator.
Machine learning
All ESET Endpoint products currently use machine learning in conjunction with all of our other layers of defense and have done so since 1997. Specifically, machine learning is used in the form of consolidated output and neural networks. For a deep inspection of the network, admins can turn on the special aggressive machine learning mode that works even without internet connection.
Multilayered defense
A single layer of defense isn't sufficient in today's constantly evolving threat landscape. All ESET endpoint products have the ability to detect malware pre-execution, during execution and post-execution. By focusing on the entire malware lifecycle, ESET provides the highest level of protection possible.
Use cases
PROBLEM
Some businesses want extra protection from ransomware attacks.
SOLUTION
- Network Attack Protection has the ability to prevent ransomware from ever infecting a system by stopping exploits at the network level.
- Our multilayered defense features an in-product sandbox with the ability to detect malware that attempts to evade detection by using obfuscation.
- Leverage ESET’s cloud malware protection system, LiveGrid®, to automatically protect against new threats without having to wait for the next detection update.
- All products contain protection in the form of Ransomware Shield to ensure that businesses are protected from malicious file encryption.

Protected by ESET since 2011.

Protected by ESET since 2016.
The ESET difference
Behavioral Detection - HIPS
ESET's Host-based Intrusion Prevention System (HIPS) monitors system activity and uses a pre-defined set of rules to recognize and stop suspicious system behavior.
Ransomware Shield
Monitors and evaluates all executed applications based on their behavior and reputation. Designed to detect and block processes that resemble the behavior of ransomware.
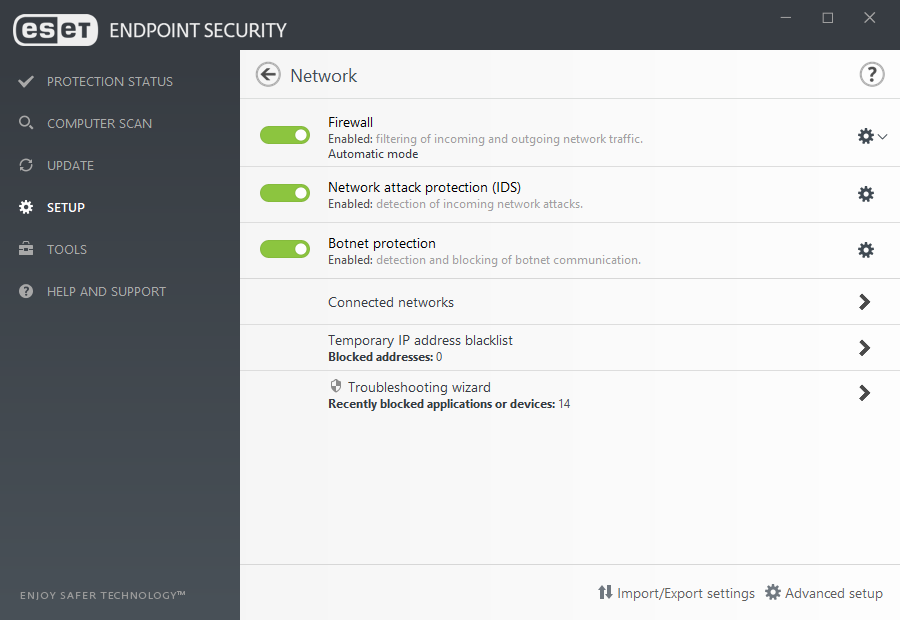
Network Attack Protection
ESET Network Attack Protection improves detection of known vulnerabilities on the network level. It constitutes another important layer of protection against spreading malware, network-conducted attacks, and exploitation of vulnerabilities for which a patch has not yet been released or deployed.
Advanced Memory Scanner
A unique ESET technology which effectively addresses an important issue of modern malware—heavy use of obfuscation and/or encryption. Advanced Memory Scanner monitors the behavior of a malicious process and scans it once it decloaks in memory.
In-product sandbox
ESET’s In-product sandbox assists in identifying the real behavior hidden underneath the surface of obfuscated malware. Utilizing this technology, ESET solutions emulate different components of computer hardware and software to execute a suspicious sample in an isolated virtualized environment.
Exploit Blocker
ESET Exploit Blocker monitors typically exploitable applications (browsers, document readers, email clients, Flash, Java, and more) and instead of just aiming at particular CVE identifiers, it focuses on exploitation techniques. When triggered, the threat is blocked immediately on the machine.
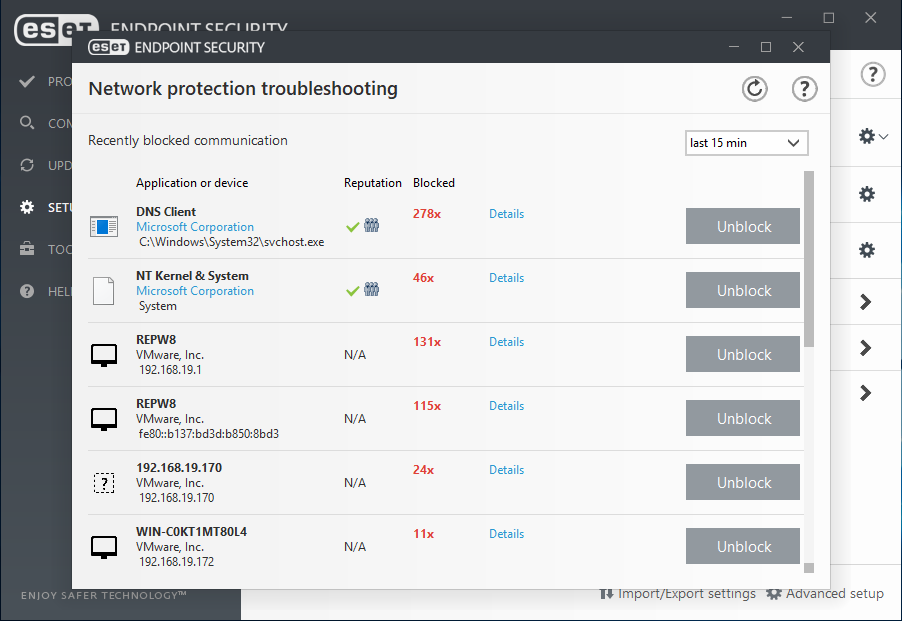
Two-way firewall
Prevents unauthorized access to the company network. It provides anti-hacker protection, data exposure prevention, and enables defining trusted networks—making all other connections, such as to public Wi-Fi, restricted by default.
Botnet Protection
ESET Botnet Protection detects malicious communication used by botnets, and at the same time identifies the offending processes. Any detected malicious communication is blocked and reported to the user.

ESET #1 in AV Comparatives Performance test in May 2019.

ESET achieved highest score in SE Labs test in Q1 2019.

ESET Endpoint Security named best business antivirus for MacOS.

ESET ranked highest by final score in VBSpam test in June 2019.
ESET ENDPOINT SECURITYFOR WINDOWS
Purchase this product as a bundle component of ESET Endpoint Protection Advanced at the same price as the individual product.
Looking for additional solutions?
Related enterprise-grade solutions

ESET Dynamic Endpoint Protection
- Security Management Center
- Endpoint Protection Platform
- Cloud Sandbox Analysis

ESET Targeted Attack Protection
- Security Management Center
- Endpoint Protection Platform
- Cloud Sandbox Analysis
- Endpoint Detection & Response
Related products and services
- ESET Security Management Center
Real-time network security visibility, reporting and management on a single screen. - ESET Dynamic Threat Defense
Cloud-based sandboxing technology detects never before seen or zero-day threats. - ESET Enterprise Inspector
EDR tool detects APTs, targeted attacks, fileless attacks. Includes risk assessment and forensic investigation. - ESET Deployment & Upgrade
Fast, seamless customer support for all new deployments or upgrades.
What IT pros are saying

"Runs better than ANY other AV I have EVER used, blocks the issues before the user can attempt to use the questionable files."
Read full review

"I enjoy the continuous protection, automatic updates, and comparably small size of this program in comparison to other options."
Read full review

"The things I enjoy most about their products is how light they run on my clients systems and how easily they are to manage and configure."
Read full review
Based on customer reviews, through G2 Crowd surveys, that asked ESET business customers to rate their experiences using ESET Endpoint Security.

"ESET is the best small footprint antivirus software out there."
Read full review

"Spend less time removing infections from endpoints by not getting them to begin with."
Read full review

"Strong antivirus defense along with ease of deployment to end users."
Read full review

See why IT pros chose ESET in the 2017 Gartner Peer Insights Customer Choice Awards for Endpoint Protection Platforms.1
Stay on top of cybersecurity news
Brought to you by respected security researchers from ESET's 13 global R&D centers.