TOTAL COST OF
OWNERSHIP CALCULATOR
Check how much your security vendor may be costing your business annually.
▼
THE TRUE COST
OF SECURITY
The cost of security is not just the cost of a licence, but the cost of managing it.
▼
FALSE POSITIVES
VENDOR COMPARISON
ESET has high detection rates and the lowest false positives.
▼
Total Cost of Ownership Calculator
Find out how much your security vendor may be costing your business every year, in addition to your licence cost.
The ESET Advantage:
World-class security technology, increased productivity with minimal system impact and low false positives.

To find out how your business can benefit from The ESET Advantage:
call us today on 01202 405 405 or complete the form below.
Unable to get data from our server. Try again later, please.
ESET respects your privacy. View our privacy policy here.
The True Cost of Security – CRN Special Report
Channel players and clients need to consider not just what a product does, but the impact of how it does it.
Download the CRN Special Report for free.
Invisible Technology
Invisible technology isn't a technology per se, but a use case for using technology without realising you are using it. Pierre Louw, Head of ESET MSP, talks about how this relates to your endpoint security.
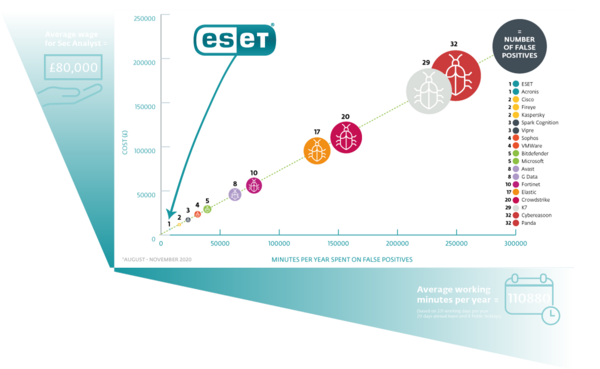
False Positives Vendor Comparison
ESET has high detection rates and the lowest false positives
False positives lead to greater costs for clients, end users and reduced security efficacy. A security analyst’s time can be expensive, and that’s time which could be spent on true positives to mitigate the risk of damaging persistent malware.

The ESET Advantage:
World-class security technology, increased productivity with minimal system impact and low false positives.
What makes our solution a perfect fit for your needs?
Endpoint protection
ESET Endpoint Security
Leverages a multilayered approach that utilises multiple technologies in dynamic equilibrium to constantly balance performance, detection and false positives, enabling organisations to:
- Protect against ransomware
- Block targeted attacks
- Prevent data breaches
- Stop fileless attacks
- Detect advanced persistent threats
- Ensure mobile protection and MDM