- ESET detected nine notable ModiLoader phishing campaigns during May 2024 in Poland, Romania, and Italy.
- These campaigns targeted small and medium-sized businesses.
- Seven of the campaigns targeted Poland, where ESET products protected over 21,000 users from these attacks.
- Attackers deployed three infostealer malware families via ModiLoader: Rescoms, Agent Tesla, and Formbook.
- Attackers used previously compromised email accounts and company servers, not only to spread malicious emails but also to host malware and collect stolen data.
BRATISLAVA — July 30, 2024 — ESET researchers investigated nine widespread phishing campaigns targeting small and medium-sized businesses (SMBs) in Poland, Romania, and Italy during May 2024, distributing various malware families. In comparison with the previous year, the attackers targeting the region shifted away from AceCryptor to ModiLoader as their delivery tool of choice and added more malware as well. Attackers used previously compromised email accounts and company servers, not only to spread malicious emails but also to host malware and collect stolen data. In May 2024 alone, ESET products protected over 26,000 users – over 21,000 (80%) of whom were in Poland – against this threat.
“In total we registered nine phishing campaigns, seven of which targeted Poland throughout May,” says Jakub Kaloč, who analysed the phishing campaigns. “The final payload to be delivered and launched on the compromised machines varied; we’ve detected campaigns delivering the information stealing Formbook; the remote access trojan and information stealer Agent Tesla; and Rescoms RAT, which is remote control and surveillance software that is able to steal sensitive information,” he adds.
In general, all the campaigns followed a similar scenario. The targeted company received an email message with a business offer. As in the phishing campaigns of H2 2023, attackers impersonated existing companies and their employees as the technique of choice to increase their campaign success rate. In this way, even if the potential victim looked for the usual red flags, they just weren’t there, and the email looked as legitimate as it could have.
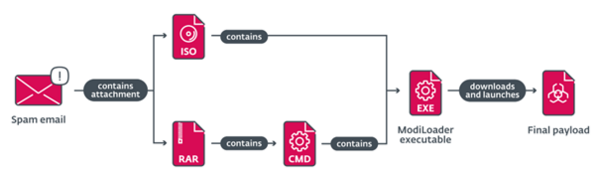
Emails from all campaigns contained a malicious attachment that the potential victim was incentivised to open, based on the text of the email. The file itself was either an ISO file or archive with the ModiLoader executable. ModiLoader is a Delphi downloader with a simple task – to download and launch malware. In two of the campaigns, ModiLoader samples were configured to download the next-stage malware from a compromised server belonging to a Hungarian company. In the rest of the campaigns, ModiLoader downloaded the next stage from Microsoft’s OneDrive cloud storage.
For more information about the ModiLoader campaigns, read the blogpost “Phishing targeting Polish SMBs continues via ModiLoader” on WeLiveSecurity-com. Make sure to follow ESET Research on Twitter (today known as X) for the latest news from ESET Research.
Chain of compromise of ModiLoader phishing campaigns in Poland during May 2024.