In ice hockey, where players collide with each other at 20 mph (30 km/h) and take shots at speeds of up to about 100 mph (161km/h), it is hard to imagine that players competed without wearing helmets until the late 1970s. Since then, this single piece of safety gear has significantly reduced injuries and prolonged careers of professional players.
This example shows that sometimes the solution to a painful problem can be quite simple. The same is true for authentication, which is among the favorite cyberattack vectors for adversaries. Relevant data confirms again and again that having a single password, no matter how strong, is not enough anymore. An additional layer of protection – multi-factor authentication (MFA) – significantly decreases the likelihood of successful attacks on user credentials.
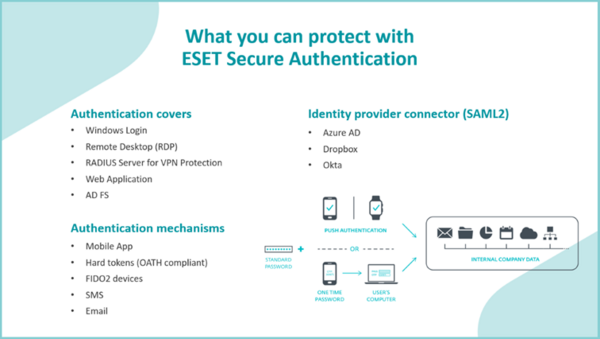
Well-developed processes to secure employees’ authentication, in combination with password hygiene, are essential parts of any prevention-first approach that aims to stop attacks before they can do any harm to a business. In pursuit of this strategy, ESET incorporated its cloud-based MFA solution ESET Secure Authentication into ESET PROTECT Hub, a new unified point of entry to the ESET PROTECT Platform serving businesses that include MSPs with user, license, and hierarchy management tools.
Aiming for the corners
Just like ice hockey players tend to aim for the top corners of the net because of a high success rate, cybercriminals know that credentials are among the most vulnerable layers of businesses’ defence because of the human element involved.
For example, despite increasing global cybersecurity awareness among adults online, the password “123456” remains the most-used credential.
And it’s not only a problem for the general public. Poor password hygiene is also observed among IT admins. Digging through more than 1.8 million pages identified as admin portals in 2023 revealed that 40,000 of them used "admin" as their password.
Knowing this, it is no surprise that the latest Verizon 2024 Data Breach Investigations Report found that 77% of basic web application attacks involved stolen credentials, 21% of them were the result of brute force (usually easily guessable passwords), and 13% of those attacks exploited vulnerabilities.
While businesses struggle with password laziness observed among their employees, adversaries improve their techniques to fool even those who are more tech savvy and vigilant. We can already see nefarious technical developments like AI-driven phishing or powerful high-end machines able to guess random six-characters-long passwords in a single day, despite the improved hashing methods used. Not to mention that users of older hashing methods can get breached instantly.
The importance of an MFA helmet
Luckily, most attackers targeting credentials behave like desperate players shooting pucks from their side across the whole rink toward their opponent’s net and hoping for the best. ”Spraying and praying” tactics are still prevalent among various cyberattacks; this is clearly demonstrated by Microsoft data published in 2023. Simple, cheap, and easily mass-produced password attacks still dominate the game. As a result, Microsoft deflects more than 1,000 password attacks per second(!) in its systems. Interestingly, they have noticed that more than 99.9% of accounts compromised didn’t have multi-factor authentication enabled.
Google found similar results in its older 2019 survey showing that adding just an another simple step of verification can block up to 100% of automated bots, 99% of bulk phishing attacks, and 66% of targeted attacks.
Last but not least: multiple or additional factors of authentication are now a standard compliance requirement, just like the helmet has become compulsory in ice hockey.
Automated attacks targeting credentials:
Phishing – Fraudulent messages, emails, or calls luring targeted users into giving their account details and passwords. Using the latest technology, including AI, it is increasingly easy to mass-produce these attacks and at the same time make them more believable.
Password spraying – Trying the most-used passwords, such as the word “password” or “1234,” against a huge number of accounts.
Dictionary attack – Trying a list of passwords derived from a dictionary of words against a valid account.
Brute force – An automated attack against a single account using all possible combinations for a password.
Breach replay or credential stuffing – Pervasive reuse of exposed credentials from previous data breaches against many accounts.
Get protected with no sweat
Available in higher tiers of the ESET PROTECT solution for businesses, ESET Secure Authentication provides an additional layer of security against common credential attacks.
It protects both regular employees and IT admins logging into business ecosystems, mitigates the risk of stolen and compromised credentials, keeps attackers from accessing corporate data, and helps businesses with cybersecurity compliance.
And the best part: reducing complexity, smooth installation and operation. The deployment takes around 10 minutes in the cloud; ESET Secure Authentication doesn’t need dedicated hardware – it's cloud-based, easily scalable, and, ESET oversees maintenance and upgrades.
Stay safe with ESET
Exploiting valid accounts is still the path of least resistance for cybercriminals, according to IBM X-Force Threat Intelligence Index 2024, and despite effective protection being available, many companies still don’t use it.
Witnessing rapid-fire strikes from cybercriminals against business accounts every second, it’s time to “put a helmet on”. With ESET PROTECT, businesses can not only enjoy multilayered and AI-powered protection against all kinds of sophisticated attacks, but also take a proactive, prevention-first approach and easily deploy MFA to defend their precious accounts against massive automated attacks.