Explore features
Ransomware and zero-day threats detection
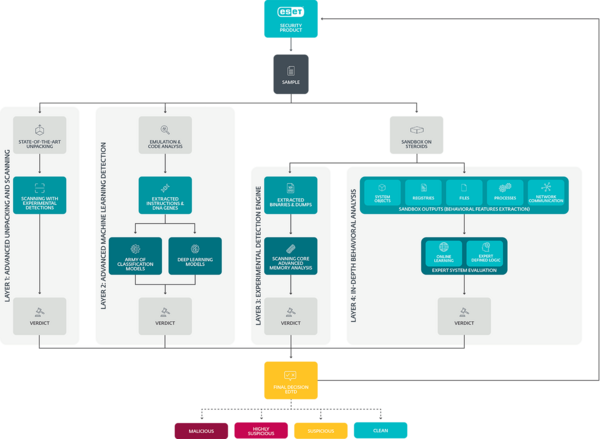
Detect new, never-before-seen types of threats. ESET utilizes three different machine learning models once a file is submitted. After that, it runs the sample through a full sandbox, simulating user behavior to trick anti-evasive techniques. Next, a deep learning neural network is used to compare the behavior seen versus historical behavioral data. Finally, the latest version of ESET's scanning engine is used to take everything apart and analyze it for anything unusual.
Granular reports
An admin can create a report from ESET Dynamic Threat Defense data in the ESET PROTECT console. They can either use one of the pre-defined reports or make a custom one.
Transparent, full visibility
Every analyzed sample status is visible in the ESET PROTECT console, which provides transparency to all data sent to ESET LiveGrid®.
Automatic protection
The endpoint or server product automatically decides whether a sample is good, bad or unknown. If the sample is unknown, it is sent to ESET Dynamic Threat Defense for analysis. Once the analysis is finished, the result is shared, and the endpoint products respond accordingly.
Mail Security protection
Not only does ESET Dynamic Threat Defense work with files, but it also works directly with ESET Mail Security, to ensure that malicious emails are not delivered to your organization.
Mobility
Nowadays, employees often do not work on the premises. Our cloud sandbox analyzes files no matter where users are.
Proactive protection
If a simple is found to be suspicious, it is blocked from executing while ESET Dynamic Threat Defense analyzes it. That way, potential threats are prevented from wreaking havoc on the system.
Tailored customization
ESET allows per-computer detailed policy configuration for ESET Dynamic Threat Defense so the admin can control what is sent and what should happen based on the receiving result.
Manual submission
At any time, a user or admin can submit samples via an ESET compatible product for analysis and get the full result. Admins will see who sent what and what the result was directly in the ESET PROTECT console.
How our advanced, multilayered analysis works
ESET Dynamic Threat Defense is a cloud-based sandboxing solution that executes all submitted suspicious samples in an isolated test environment and evaluates their behavior using threat intelligence feeds, ESET’s multiple internal tools for static and dynamic analysis, and reputation data to detect zero-day threats. Four layers are used to analyze samples, but not all of these have to be used if we’re sure about the result in advance.