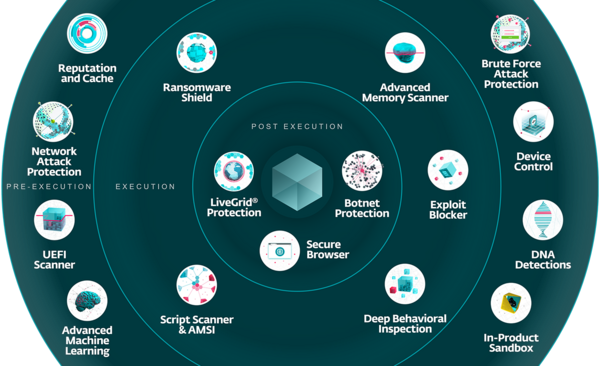
Multilayered security
Our global research labs drive the development of ESET's unique protection.
Various core ESET technologies come into play of detecting and blocking a threat at different times on a protected device:
Antivirus and Antispyware
Provides proactive protection against all types of online and offline threats and prevents malware spreading to other users.
Advanced Machine Learning
In addition to ESET Machine Learning in the cloud, this proactive layer runs locally. It is specifically designed to detect advanced, never-before-seen malware, while having a low impact on performance.
Idle-State Scanning
Aids system performance by performing in-depth scans when your computer is not in use.Helps detect potential inactive threats before they can cause damage.
Exploit Blocker
Blocks attacks specifically designed to evade antivirus detection, and eliminates lockscreens and ransomware. Protects against attacks on web browsers, PDF readers and other applications, including Java-based software.
Cloud-Powered Scanning
Speeds up scans by whitelisting safe files based on the ESET LiveGrid® file reputation database. Helps to proactively stop unknown malware based on its behavior, by comparing it with our cloud-based reputation system.
Script-Based Attack Protection
Detects attacks by malicious scripts that try to exploit Windows PowerShell.Also detects malicious JavaScripts that can attack via your browser. Mozilla Firefox, Google Chrome, Microsoft Internet Explorer and Microsoft Edge browsers are all supported.
System Registry Scanner
Looks for references to infected files or malware embedded as data in the Windows System Registry, a hierarchical database that stores low-level settings for the Microsoft Windows operating system and for applications that opt to use the registry.
Brute Force Attack Protection
Blocks brute-force attacks, a method of discovering a targeted password by systematically trying all combinations of letters, numbers, and symbols.
Scan While Downloading Files
Decreases scanning time by scanning specific file types − such as archives − during the download process.
Ransomware Shield
Blocks malware that tries to lock you out of your personal data in order to demand a ‘ransom’ payment. Employs advanced behavior-based detection techniques to protect against malware that tries to damage devices by encrypting as many files as it can locate on local and network drives.
Intel® Threat Detection Technology NEW
Boosts ransomware protection by integrating Intel’s hardware-based ransomware detection technology. It helps to expose ransomware as it attempts to avoid detection in memory. This enablement also allows us to use Intel® TDT machine learning models, which are only found on Intel® Core™ processors, to assist with the detection of threats using advanced evasion techniques, including zero-day variants, binary obfuscation, cloaking in a virtual machine, and fileless attacks, while keeping overall system performance high across all compute layers.
Host-Based Intrusion Prevention System (HIPS)
Lets you customize the behavior of the system in greater detail, with a focus on behavioral detection. Gives you the option to specify rules for system registry, active processes and programs in order to fine-tune your security posture. Employs the latest tracing capabilities to scan parts of memory that can be modified by sophisticated malware injection techniques.
WMI Scanner
Looks for references to infected files or malware embedded as data in Windows Management Instrumentation, a set of tools that manages devices and applications in a Windows environment.
Advanced Memory Scanner
Enables improved detection of persistent malware that employs multiple layers of encryption to conceal its activity.
UEFI Scanner
Protects from threats that attack your computer on a deeper level, even before Windows starts - on systems with the UEFI system interface.
ESET LiveGuard Not included
A new service that is personalized to you, designed to discover and stop never-before-seen types of threats. Handles a wide range of file types, including documents, scripts, installers and executable files. Suspicious files are run in a safe, sandboxed environment within the ESET HQ Cloud.