Protection for home 


Choose a plan that’s right for you.
Custom solutions:

Powerful protection, small-business savvy.
Renew your ESET subscription and save.
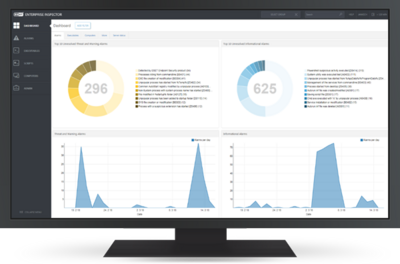
Effortlessly manage your security from one space.
Download
Get your ESET protection up and running.
Download your protection now.
Claim your FREE 30-day trial today.
Why ESET?
Over 30 years of science-driven innovation.
Focus on what matters—leave the rest to us.
Customer zone
Effortlessly manage your security from one space.
Business accounts activated after August 1, 2024.
Log in to
ESET BUSINESS ACCOUNT
Business accounts activated before July 31, 2024.