
What is Kr00k?
Kr00k – formally known as CVE-2019-15126 – is a vulnerability in Broadcom and Cypress Wi-Fi chips that allows unauthorized decryption of some WPA2-encrypted traffic.
Who is affected?
The vulnerability affects all unpatched devices with Broadcom and Cypress FullMac Wi-Fi chips. These are the most common Wi-Fi chips used in today's client devices, made by well-known manufacturers including Amazon (Echo, Kindle), Apple (iPhone, iPad, MacBook), Google (Nexus), Samsung (Galaxy) as well as devices under many other brands.
Wi-Fi Access points and routers are also affected by Kr00k, making even environments with patched client devices vulnerable. All-in-all, before patching there were more than a billion affected devices.
Which Wi-Fi chips exactly were vulnerable?
ESET tested a number of popular devices with Broadcom and Cypress Wi-Fi chips and confirmed a manifestation of the Kr00k vulnerability. We have also tested some devices with Wi-Fi chips from other manufacturers, including Qualcomm, Realtek, Ralink and Mediatek, and did not see the vulnerability manifest itself. Obviously, we have not tested every possible Wi-Fi chip by every manufacturer, so while we are not aware of other affected chips, we also cannot rule this out.
How do I know if I’m still vulnerable to Kr00k?
Make sure you have updated all your Wi-Fi capable devices, including phones, tablets, laptops, and Wi-Fi access points and routers to the latest operating system, software and/or firmware versions. According to our information, patches for devices by major manufacturers have been released by now.
Inquiries whether your devices with affected chips have been patched - or if your device uses the affected chips in the first place - need to be directed at your device manufacturer.
I’m a device manufacturer: Have my devices been patched?
Please inquire about patches for the Kr00k vulnerability directly with your chip manufacturer.
ESET is also working with the Wi-Fi Alliance, which is developing additional tools that might help organizations identify vulnerable devices in their infrastructure.
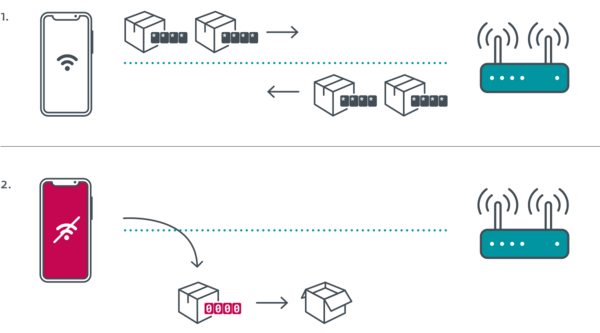
What is the state of patching of Kr00k?
As this vulnerability affects Wi-Fi chips used in devices manufactured by various vendors, the patching process involves both the chip manufacturers (Broadcom and Cypress), as well as the device manufacturers. ESET responsibly disclosed the identified vulnerability to Broadcom and Cypress, who subsequently released patches to the individual device manufacturers.
Furthermore, to expand the scope of our responsible disclosure, ESET has worked with ICASI to ensure that all possibly affected device manufacturers are aware of Kr00k.
Released patches:
While we don’t have a comprehensive overview of when all these vendors have subsequently released software updates (due to the large number), we are aware of the following:
Released patches:
- iOS 13.2 and iPadOS 13.2 – October 28, 2019
- macOS Catalina 10.15.1, Security Update 2019-001, and Security Update 2019-006 – October 29, 2019
- macOS Catalina 10.15.2, Security Update 2019-002, Security Update 2019-007 – December 10, 2019
- Cisco Security Advisory 20200226 – February 27, 2020
- Mist Security Advisory – Kr00k Attack & FAQ – February 27, 2020
- Aruba Security Advisory ARUBA-PSA-2020-003 – February 28, 2020
- Huawei Security Notice 20200228-01 – February 28, 2020
- Zebra Security Alert – March 2nd, 2020
Inquiries about patching of devices by other manufacturers need to be directed to the respective manufacturers.
Where can I find more information?
For more details, please read ESET's Kr00k white paper published at WeLiveSecurity.com. ESET researchers presented the results of this research at RSA 2020.
Additional information
Wait, what? Can someone break into my encrypted wireless network traffic?
Yes, that is the case if your device is not patched yet. Fortunately, there are a few aspects that limit the impact of the bug:
- Firstly, it's a vulnerability concerning encryption on the wireless LAN (Wi-Fi) layer. It has nothing to do with TLS - the encryption that secures your online banking, email, and any website prefixed with HTTPS. In other words, a successful attack exploiting Kr00k degrades your security a step towards what you'd have on an open Wi-Fi network.
- Secondly, as it's tied to Wi-Fi, the attacker would have to be in close proximity to your Wi-Fi signal. (But - wouldn't need to know your Wi-Fi password!)
How easy/difficult is it to exploit Kr00k?
Eavesdropping on the communication of an unpatched device is simple enough for most black-hat actors.
Does Kr00k affect my Wi-Fi password? Should I change it?
Kr00k is in no way tied to your Wi-Fi password, therefore the vulnerability does not affect its security and changing it does not hamper the ability of attackers trying to exploit the vulnerability.
Which wireless security protocols are affected (WEP, WPA, WPA2, WPA3)?
Our research has focused on the most ubiquitous protocol WPA2 with CCMP. The outdated and insecure WEP, WPA-TKIP, and the new WPA3 protocols, were not the focus of our research.
Does Kr00k affect just client devices or access points too?
Unfortunately, Kr00k also affects access points, meaning even communication between patched client devices and such vulnerable access points can be intercepted.
Who discovered the vulnerability?
ESET Experimental Research and Detection Team, most prominently ESET security researcher Miloš Čermák.

