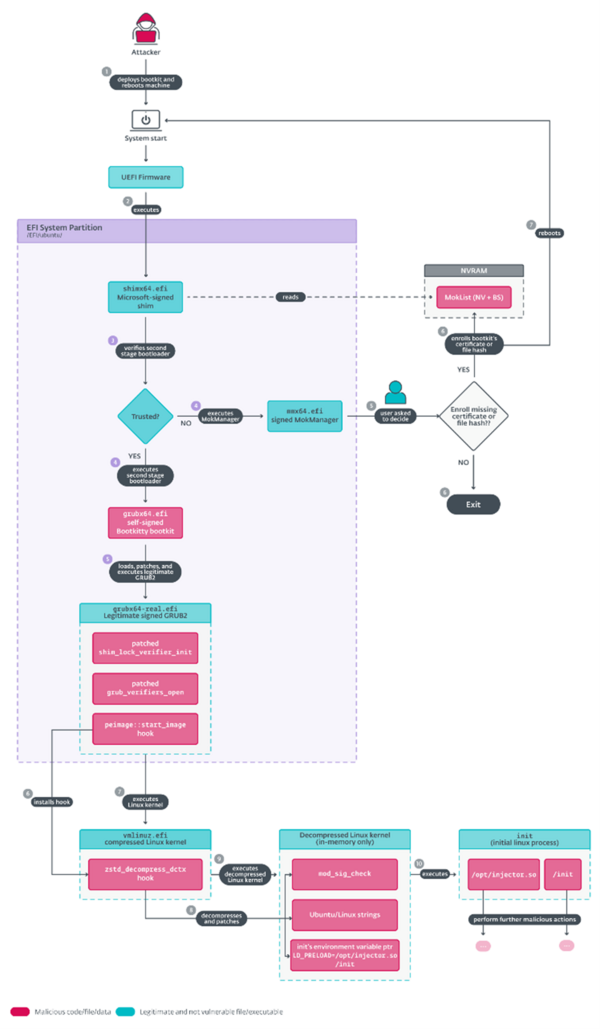
- In November 2024, a previously unknown application, named bootkit.efi, was uploaded to VirusTotal, upon inspection ESET Research discovered it to be an UEFI application.
- Further analysis confirmed that it is a UEFI bootkit, named Bootkitty by its creators; surprisingly, it's the first UEFI bootkit to target Linux – specifically, several Ubuntu versions. The bootkit contains many artifacts, suggesting that this is more like a proof of concept than the work of a threat actor.
- ESET Research also discovered a possibly related kernel module, which we named BCDropper, that deploys an Executable and Linking Format (ELF) Linux program responsible for loading another kernel module.
BRATISLAVA — November 27, 2024 — ESET research has discovered the first UEFI bootkit designed for Linux systems, named Bootkitty by its creators. ESET believes this bootkit is likely an initial proof of concept, and based on ESET telemetry, it has not been deployed in the wild. However, it is the first evidence that UEFI bootkits are no longer confined to Windows systems alone. The bootkit’s main goal is to disable the kernel’s signature verification feature and to preload two as yet unknown ELF binaries via the Linux “init” process (which is the first process executed by the Linux kernel during system startup).
The previously unknown UEFI application, named “bootkit.efi”, was uploaded to VirusTotal. Bootkitty is signed by a self-signed certificate, thus is not capable of running on systems with UEFI Secure Boot enabled by default. However, Bootkitty is designed to boot the Linux kernel seamlessly, whether UEFI Secure Boot is enabled or not, as it patches, in memory, the necessary functions responsible for integrity verification.
The bootkit is an advanced rootkit that is capable of replacing the boot loader, and of patching the kernel ahead of its execution. Bootkitty allows the attacker to take full control over the affected machine, as it co-opts the machine’s booting process and executes malware before the operating system has even started.
During the analysis, ESET discovered a possibly related unsigned kernel module that ESET named BCDropper – with signs suggesting that it could have been developed by the same author(s) as Bootkitty. It deploys an ELF binary responsible for loading yet another kernel module unknown at the time of analysis.
“Bootkitty contains many artifacts suggesting that this is more like a proof of concept than the work of an threat actor. Even though the current version from VirusTotal does not, at the moment, represent a real threat to the majority of Linux systems since it can affect only a few Ubuntu versions, it emphasizes the necessity of being prepared for potential future threats,” says ESET researcher Martin Smolár, who analyzed Bootkitty. “To keep your Linux systems safe from such threats, make sure that UEFI Secure Boot is enabled, your system firmware, security software and OS are up-to-date, and so is your UEFI revocations list,” he adds.
After booting up a system with Bootkitty in the ESET testing environment, researchers noticed that the kernel was marked as tainted (a command can be used to check the tainted value), which was not the case when the bootkit was absent. Another way to tell whether the bootkit is present on the system with UEFI Secure Boot enabled is by attempting to load an unsigned dummy kernel module during runtime. If it’s present, the module will be loaded; if not – the kernel refuses to load it. A simple remedy to get rid of the bootkit, when the bootkit is deployed as "/EFI/ubuntu/grubx64.efi”, is to move the legitimate “/EFI/ubuntu/grubx64-real.efi” file back to its original location, which is “/EFI/ubuntu/grubx64.efi”.
Over the past few years, the UEFI threat landscape, particularly that of UEFI bootkits, has evolved significantly. It all started with the first UEFI bootkit proof of concept (PoC) described by Andrea Allievi in 2012, which served as a demonstration of deploying bootkits on modern UEFI-based Windows systems, and was followed with many other PoCs (EfiGuard, Boot Backdoor, UEFI-bootkit). It took several years until the first two real UEFI bootkits were discovered in the wild (one of those was ESPecter in 2021 by ESET), and it took two more years until the infamous BlackLotus – the first UEFI bootkit capable of bypassing UEFI Secure Boot on up-to-date systems – appeared (in 2023 discovered by ESET). A common thread among these publicly known bootkits was their exclusive targeting of Windows systems.
For a more detailed analysis and technical breakdown of Bootkitty, the first bootkit for Linux, check out the latest ESET Research blogpost “Bootkitty: Analyzing the first UEFI bootkit for Linux” on WeLiveSecurity.com. Make sure to follow ESET Research on Twitter (today known as X) for the latest news from ESET Research.
Bootkitty execution overview
About ESET
ESET® provides cutting-edge digital security to prevent attacks before they happen. By combining the power of AI and human expertise, ESET stays ahead of known and emerging cyberthreats — securing businesses, critical infrastructure, and individuals. Whether it’s endpoint, cloud or mobile protection, our AI-native, cloud-first solutions and services remain highly effective and easy to use. ESET technology includes robust detection and response, ultra-secure encryption, and multifactor authentication. With 24/7 real-time defense and strong local support, we keep users safe and businesses running without interruption. An ever-evolving digital landscape demands a progressive approach to security: ESET is committed to world-class research and powerful threat intelligence, backed by R&D centers and a strong global partner network. For more information, visit www.eset.com or follow us on LinkedIn, Facebook, and X.