- ESET researchers discovered two previously unknown vulnerabilities, one in Mozilla and the other in Windows, being exploited by the Russia-aligned RomCom Advanced persistent threat (APT) group.
- Analysis of the exploit led to the discovery of the first vulnerability, now assigned CVE-2024-9680: a use-after-free bug in the animation timeline feature in Firefox. ESET reported the vulnerability to Mozilla on October 8, 2024; it was patched within a day.
- This critical vulnerability has a score of 9.8 out of 10.
- Further analysis revealed another zero-day vulnerability in Windows: a privilege escalation bug, now assigned CVE 2024 49039, that allows code to run outside of Firefox's sandbox. Microsoft released a patch for this second vulnerability on November 12, 2024.
- The two zero-day vulnerabilities chained together armed RomCom with an exploit that requires no user interaction other than browsing to a specially crafted website.
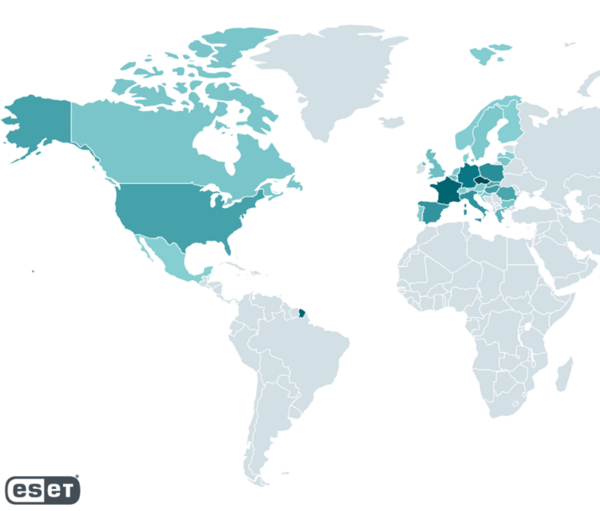
- Potential victims who visited websites hosting the exploit were located mostly in Europe and North America.
MONTREAL, BRATISLAVA — November 26, 2024 — ESET researchers discovered a previously unknown vulnerability, CVE-2024-9680, in Mozilla products, exploited in the wild by Russia-aligned APT group RomCom. Further analysis revealed another zero-day vulnerability in Windows: a privilege escalation bug, now assigned CVE-2024-49039. In a successful attack, if a victim browses a web page containing the exploit, an adversary can run arbitrary code – without any user interaction required (zero click) – which in this case led to the installation of RomCom’s backdoor on the victim’s computer. The backdoor used by the group is capable of executing commands and downloading additional modules to the victim’s machine. The Mozilla-related critical vulnerability discovered by ESET Research on October 8 has a CVSS score of 9.8 on a scale from 0 to 10. In 2024, RomCom struck in Ukraine and other European countries, as well as the United States. According to our telemetry, from October 10, 2024 to November 4th, 2024, potential victims who visited websites hosting the exploit were located mostly in Europe and North America.
On October 8, 2024, ESET researchers discovered vulnerability CVE-2024-9680. It is a use-after-free bug in the animation timeline feature in Firefox. Mozilla patched the vulnerability on October 9, 2024. Further analysis revealed another zero-day vulnerability, in Windows: a privilege escalation bug, now assigned CVE 2024 49039, that allows code to run outside Firefox’s sandbox. Microsoft released a patch for this second vulnerability on November 12, 2024.
The vulnerability CVE-2024-9680 discovered on October 8 allows vulnerable versions of Firefox, Thunderbird, and the Tor Browser to execute code in the restricted context of the browser. Chained with the previously unknown vulnerability in Windows, CVE-2024-49039, which has a CVSS score of 8.8, arbitrary code can be executed in the context of the logged-in user. Chaining together two zero-day vulnerabilities armed RomCom with an exploit that requires no user interaction. This level of sophistication demonstrates the threat actor’s intent and means to obtain or develop stealthy capabilities. Furthermore, successful exploitation attempts delivered the RomCom backdoor in what looks like a widespread campaign.
RomCom (also known as Storm-0978, Tropical Scorpius, or UNC2596) is a Russia-aligned group that conducts both opportunistic campaigns against selected business verticals and targeted espionage operations. The group’s focus has shifted to include espionage operations collecting intelligence, in parallel with its more conventional cybercrime operations. In 2024, ESET discovered cyberespionage and cybercrime operations of RomCom against governmental entities, defense, and energy sectors in Ukraine, the pharmaceutical and insurance sectors in the US; the legal sector in Germany; and governmental entities in Europe.
“The compromise chain is composed of a fake website that redirects the potential victim to the server hosting the exploit, and should the exploit succeed, shellcode is executed that downloads and executes the RomCom backdoor. While we don’t know how the link to the fake website is distributed, however, if the page is reached using a vulnerable browser, a payload is dropped and executed on the victim’s computer with no user interaction required,” says ESET researcher Damien Schaeffer, who discovered both vulnerabilities. “We would like to thank the team at Mozilla for being very responsive and to highlight their impressive work ethic to release a patch within a day,” he adds. Each vulnerability was fixed by, respectively, Mozilla and Microsoft.
This is at least the second time that RomCom has been caught exploiting a significant zero-day vulnerability in the wild, after the abuse of CVE-2023-36884 via Microsoft Word in June 2023.
For a more detailed analysis and technical breakdown of the discovered vulnerabilities, check out the latest ESET Research blogpost “RomCom exploits Firefox and Windows zero days in the wild” on WeLiveSecurity.com. Make sure to follow ESET Research on Twitter (today known as X) for the latest news from ESET Research.
Heatmap of potential victims
About ESET
ESET® provides cutting-edge digital security to prevent attacks before they happen. By combining the power of AI and human expertise, ESET stays ahead of known and emerging cyberthreats — securing businesses, critical infrastructure, and individuals. Whether it’s endpoint, cloud or mobile protection, our AI-native, cloud-first solutions and services remain highly effective and easy to use. ESET technology includes robust detection and response, ultra-secure encryption, and multifactor authentication. With 24/7 real-time defense and strong local support, we keep users safe and businesses running without interruption. An ever-evolving digital landscape demands a progressive approach to security: ESET is committed to world-class research and powerful threat intelligence, backed by R&D centers and a strong global partner network. For more information, visit www.eset.com or follow us on LinkedIn, Facebook, and X.