- ESET Research discovers the CloudScout toolset, detected in Taiwan between 2022 and 2023, in the networks of a religious institution and a government entity.
- The toolset is used by the China-aligned Evasive Panda group for cyberespionage.
- CloudScout utilizes stolen cookies, provided by MgBot plugins, to access and exfiltrate data stored on various cloud services.
- We analyzed three CloudScout modules, which aim to steal data from Google Drive, Gmail, and Outlook. We believe that at least seven additional modules exist.
MONTREAL, BRATISLAVA — October 28, 2024 — ESET researchers discovered a previously undocumented toolset used by the China-aligned group, Evasive Panda, to access and retrieve data from cloud services such as Google Drive, Gmail, and Outlook. The post-compromise toolset CloudScout was used to target a government entity and a religious organization in Taiwan from 2022 to 2023. Aiming at cyberespionage, CloudScout is capable of retrieving data from various cloud services by leveraging stolen web session cookies.
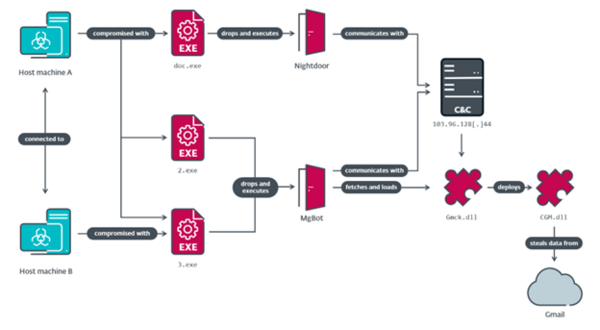
Evasive Panda deployed three previously unknown .NET modules designed to access public cloud services by hijacking authenticated web sessions. This technique relies on stealing cookies from a web browser database, and then using them in a specific set of web requests to gain access to cloud services. Unlike stolen credentials, which may be blocked by security features such as two-factor authentication (2FA) and IP tracking, stolen web session cookies allow the attacker, right from the victim’s machine, to retrieve data stored in the cloud. CloudScout is implemented as an extension to MgBot backdoor plugins. Hardcoded fields in CloudScout’s web requests for stealing Outlook email messages suggest that the samples involved were crafted to target Taiwanese users.
In May 2022, the network of a Taiwanese religious institution was compromised with MgBot and Nightdoor. In this incident, MgBot was used to install a plugin that deploys a CloudScout module. In February 2023, CloudScout modules and the Nightdoor implant were detected at what we suspect is a Taiwanese government entity.
After authentication, the CloudScout modules browse the compromised cloud service accounts in a manner similar to how a regular user would in a web browser. To achieve this, each CloudScout module is equipped with a set of hardcoded web requests to perform, along with complex HTML parsers, that identify and extract the data of interest from the web responses. The data is exfiltrated and in the final step, the CloudScout modules do a full cleanup, removing all artifacts generated during the collection cycle except the files to be exfiltrated. After that, they either exit or continue and wait for a new configuration file to start a new collection cycle.
“The professional design behind the CloudScout framework demonstrates Evasive Panda’s technical capabilities and the important roles that cloud-stored documents, user profiles, and email play in its espionage operations,” explains ESET researcher Anh Ho, who discovered CloudScout.
Evasive Panda (also known as BRONZE HIGHLAND, Daggerfly, or StormBamboo) is a China-aligned APT group, operating since at least 2012. Evasive Panda’s objective is cyberespionage against countries and organizations opposing China’s interests through independence movements such as those in the Tibetan diaspora, religious and academic institutions in Taiwan and in Hong Kong, and supporters of democracy in China. At times, ESET has also observed its cyberespionage operations extend to countries such as Vietnam, Myanmar, and South Korea. Evasive Panda has accumulated an impressive list of attack vectors. We have seen its operators conduct sophisticated TTPs such as supply-chain and watering-hole attacks, and DNS hijacking.
For a more detailed analysis and technical breakdown of CloudScout, check out the latest ESET Research blogpost “CloudScout: Evasive Panda scouting cloud services” on WeLiveSecurity.com. Make sure to follow ESET Research on Twitter (today known as X) for the latest news from ESET Research.
Compromise chain observed in the network of a religious institution in Taiwan
About ESET
ESET® provides cutting-edge digital security to prevent attacks before they happen. By combining the power of AI and human expertise, ESET stays ahead of known and emerging cyberthreats — securing businesses, critical infrastructure, and individuals. Whether it’s endpoint, cloud or mobile protection, our AI-native, cloud-first solutions and services remain highly effective and easy to use. ESET technology includes robust detection and response, ultra-secure encryption, and multifactor authentication. With 24/7 real-time defense and strong local support, we keep users safe and businesses running without interruption. An ever-evolving digital landscape demands a progressive approach to security: ESET is committed to world-class research and powerful threat intelligence, backed by R&D centers and a strong global partner network. For more information, visit www.eset.com or follow us on LinkedIn, Facebook, and X.