- In Operation Magnus just days ago, Dutch National police, alongside the FBI, Eurojust, and several other law enforcement organizations, performed a takedown of the infamous RedLine Stealer.
- In 2023, ESET researchers, in collaboration with law enforcement, collected multiple modules used to run the infrastructure behind the RedLine Stealer operation.
- We analyzed these previously undocumented modules to provide insight into the internal workings of this malware-as-a-service empire.
- We were able to identify over 1,000 unique IP addresses used to host RedLine control panels.
- Based on our analysis of the source code and backend samples, ESET has determined that RedLine Stealer and another META Stealer share the same creator.
- RedLine Stealer can collect a large variety of information, including local cryptocurrency wallets; cookies, saved credentials, and saved credit card details from browsers; and saved data from Steam, Discord, Telegram, and various desktop VPN applications.
BRATISLAVA — November 5, 2024 — Following the takedown of RedLine Stealer by international authorities, ESET researchers are publicly releasing their research into this infostealer’s undocumented backend modules. The in-depth technical analysis provides a greater understanding of the inner workings of this malware-as-a-service (MaaS) empire. ESET researchers, in collaboration with law enforcement, collected multiple modules used to run the infrastructure behind RedLine Stealer in 2023. The Dutch National police, alongside the FBI, Eurojust, and several other law enforcement organizations, performed a takedown of the infamous RedLine Stealer operation and its clone called META Stealer on October 24, 2024. This global effort, named Operation Magnus, resulted in the takedown of three servers in the Netherlands, the seizure of two domains, two people being taken into custody in Belgium, and the unsealing of charges against one of the alleged perpetrators in the United States.
Back in April 2023, ESET participated in a partial disruption operation of the RedLine malware, which consisted of the removal of several GitHub repositories used as dead-drop resolvers for the malware’s control panel. Around that time, ESET Research investigated previously undocumented backend modules of this malware family in collaboration with fellow researchers at Flare. These modules don’t interact directly with the malware, but rather handle authentication and provide functionality for the control panel.
“We were able to identify over 1,000 unique IP addresses used to host RedLine control panels. The 2023 versions of RedLine Stealer ESET investigated in detail used the Windows Communication Framework for communication between the components, while the latest version from 2024 uses a REST API. Based on our analysis of the source code and backend samples, we have determined that RedLine Stealer and META Stealer share the same creator,” says ESET researcher Alexandre Côté Cyr, who investigated the RedLine and META stealers.
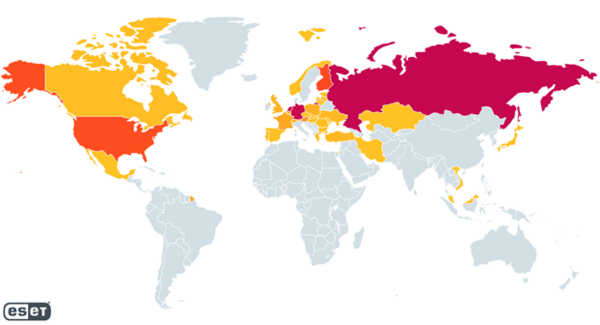
Those unique IP addresses were used to host RedLine panels and of these hosted panels, Russia, Germany, and the Netherlands each account for about 20% of the total, while Finland and the United States each represent around 10%. RedLine compromises are usually opportunistic rather than targeted. ESET was also able to identify multiple distinct back-end servers. Based on their geographical distribution, the servers are mainly located in Russia (about a third of them) while the UK, the Netherlands, and the Czech Republic each represent around 15% of the servers we identified.
RedLine Stealer is information-stealing malware first discovered in 2020, and rather than being centrally operated, RedLine operates on a MaaS model in which anyone can buy a turnkey infostealer solution from various online forums and Telegram channels. Clients, which we refer to as affiliates, can opt for a monthly subscription, or a lifetime license; in exchange for their money, they get a control panel that generates malware samples and acts as a C&C server for them. The generated samples can collect a large variety of information, including local cryptocurrency wallets; cookies, saved credentials, and saved credit card details from browsers; and saved data from Steam, Discord, Telegram, and various desktop VPN applications.
“Using a ready-made solution makes it easier for the affiliates to integrate RedLine Stealer into larger campaigns. Some notable examples include posing as free downloads of ChatGPT in 2023 and masquerading as video game cheats in the first half of 2024,” explains Côté Cyr.
Before Operation Magnus, RedLine was among the most widespread of infostealer malware with a very large number of affiliates using its control panel. However, the malware-as-a-service enterprise seems to be orchestrated by only a small number of people, some of whom have now been identified by law enforcement.
You can read detailed technical analysis in research blogpost “Life on a crooked RedLine: Analyzing the infamous infostealer’s backend” on WeLiveSecurity.com. Make sure to follow ESET Research on Twitter (today known as X) for the latest news from ESET Research.
Heatmap showing the geographical distribution of hosted RedLine panels
About ESET
ESET® provides cutting-edge digital security to prevent attacks before they happen. By combining the power of AI and human expertise, ESET stays ahead of known and emerging cyberthreats — securing businesses, critical infrastructure, and individuals. Whether it’s endpoint, cloud or mobile protection, our AI-native, cloud-first solutions and services remain highly effective and easy to use. ESET technology includes robust detection and response, ultra-secure encryption, and multifactor authentication. With 24/7 real-time defense and strong local support, we keep users safe and businesses running without interruption. An ever-evolving digital landscape demands a progressive approach to security: ESET is committed to world-class research and powerful threat intelligence, backed by R&D centers and a strong global partner network. For more information, visit www.eset.com or follow us on LinkedIn, Facebook, and X.