
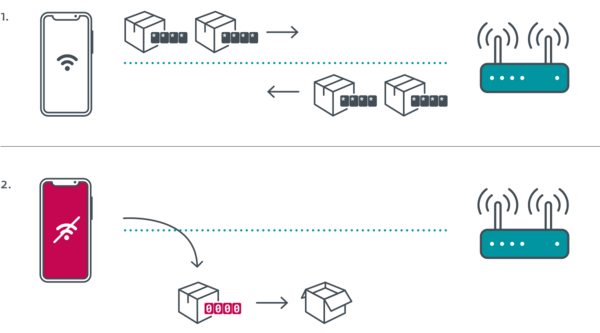
What is Kr00k?
Kr00k – formally known as CVE-2019-15126 – is a vulnerability in Broadcom and Cypress Wi-Fi chips that allows unauthorized decryption of some WPA2-encrypted traffic.
Who is affected?
The vulnerability affects all unpatched devices with Broadcom and Cypress FullMac Wi-Fi chips. These are the most common Wi-Fi chips used in today's client devices, made by well-known manufacturers including Amazon (Echo, Kindle), Apple (iPhone, iPad, MacBook), Google (Nexus), Samsung (Galaxy) as well as devices under many other brands.
Wi-Fi Access points and routers are also affected by Kr00k, making even environments with patched client devices vulnerable. All-in-all, before patching there were more than a billion affected devices.
Which Wi-Fi chips exactly were vulnerable?
How do I know if I’m still vulnerable to Kr00k?
Make sure you have updated all your Wi-Fi capable devices, including phones, tablets, laptops, and Wi-Fi access points and routers to the latest operating system, software and/or firmware versions. According to our information, patches for devices by major manufacturers have been released by now.
Inquiries whether your devices with affected chips have been patched - or if your device uses the affected chips in the first place - need to be directed at your device manufacturer.
I’m a device manufacturer: Have my devices been patched?
What is the state of patching of Kr00k?
As this vulnerability affects Wi-Fi chips used in devices manufactured by various vendors, the patching process involves both the chip manufacturers (Broadcom and Cypress), as well as the device manufacturers. ESET responsibly disclosed the identified vulnerability to Broadcom and Cypress, who subsequently released patches to the individual device manufacturers.
Furthermore, to expand the scope of our responsible disclosure, ESET has worked with ICASI to ensure that all possibly affected device manufacturers are aware of Kr00k.
Released patches:
While we don’t have a comprehensive overview of when all these vendors have subsequently released software updates (due to the large number), we are aware of the following:
Vendor advisories:
Apple iOS 13.2 and iPadOS 13.2 – October 28, 2019
Apple macOS Security Update 2019-001, and Security Update 2019-006 – October 29, 2019
Apple macOS Security Update 2019-002, Security Update 2019-007 – December 10, 2019
Aruba Security Advisory ARUBA-PSA-2020-003 – February 28, 2020
Asus Security Advisory - March 18, 2020
Cisco Security Advisory 20200226 – February 27, 2020
Crestron Security Advisory AM-100-101 – March 9, 2020
D-Link Security Bulletin - Kr00k ESET - March 9, 2020
Huawei Security Notice 20200228-01 – February 28, 2020
Microchip Security Advisory – March 4, 2020
Mist Security Advisory – Kr00k Attack & FAQ – February 27, 2020
Samsung Mobile Security Post – February 27, 2020
Thomas Krenn Security Advisory for Kr00k – February 27, 2020
Zebra Security Alert – March 2nd, 2020
Inquiries about patching of devices by other manufacturers need to be directed to the respective manufacturers.
Where can I find more information?
For more details, please read ESET's Kr00k white paper published at WeLiveSecurity.com. ESET researchers presented the results of this research at RSA 2020.

