LAST UPDATED 3:40 p.m. EDT:
A massive new ransomware attack that started in Ukraine is spreading across Europe and the United States, according to Reuters and multiple other sources. Prominent companies that have been affected are the Danish shipping company Maersk and the British advertising company WPP.
The ransomware appears to be related to the Petya family, which is currently detected by ESET as Win32/Diskcoder.C Trojan.
ESET users can find instructions to ensure the highest level of protection against this threat here. In addition, here is an advisory for ESET customers about the new malware. ESET protects against this threat, provided you have a default install of any modern ESET product. Additionally, any ESET product with network detection protects against the SMB spreading mechanism, EternalBlue, proactively.
The scale of the attack is being compared to the recent WannaCry outbreak. ESET protects both businesses and home users against WannaCry.
ESET researchers have located the point from which this global epidemic has all started. Attackers have successfully compromised the accounting software M.E.Doc, popular across various industries in Ukraine, including financial institutions. Several of them executed a trojanized update of M.E.Doc, which allowed attackers to launch the massive ransomware campaign today which spread across the whole country and to the whole world. M.E.Doc has today released a warning on their website: http://www.me-doc.com.ua/vnimaniyu-polzovateley.
How does Petya work?
The Petya malware attacks a computer’s MBR (master boot record), a key part of the startup system that contains information about the hard disk partitions and helps load the operating system. If the malware successfully infects the MBR, it will encrypt the whole drive itself. Otherwise, it encrypts all files, like Mischa.
The new malware appears to be using a combination of the EternalBlue exploit used by WannaCryptor for getting inside the network, then spreading through PsExec for spreading within it.
To check if your Windows operating system is patched against it, use ESET's free EternalBlue Vulnerability Checker.
This powerful combination is likely the reason why the outbreak is spreading quickly, even after previous outbreaks have generated headlines and most vulnerabilities should have been patched. It only takes one unpatched computer to get inside the network. From there, the malware can take over administrator rights and spread to other computers.
Petya and crypto-ransomware
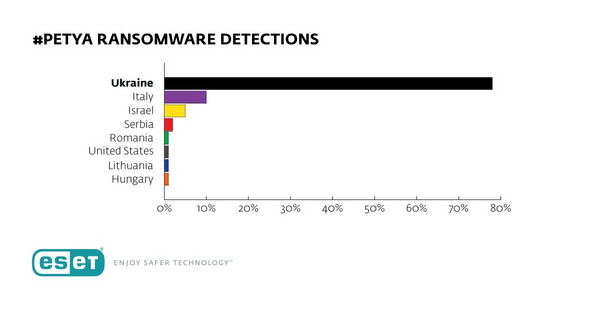
In Ukraine, the financial sector, energy sector and numerous other industries have been hit. The scope of the damage caused to the energy sector is not yet confirmed, and there has been no reports of a power outage, as was the case previously with the infamous Industroyer malware that was discovered by ESET.
An image that reportedly shows the ransomware message is making the rounds online, including one from Group-IB with the following message (which we’ve paraphrased):
“If you see this text, then your files are no longer accessible, because they have been encrypted … We guarantee that you can recover all your files safely and easily. All you need to do is submit the payment [$300 bitcoins] and purchase the decryption key.”
For more on Petya and crypto-ransomware, see this article from 2016 from ESET’s WeLiveSecurity.com blog.
This blog post will be updated as new information comes in.
