Authentication mechanisms are a vital aspect of cybersecurity deserving adequate protection, but increasing complexity makes them an easier target.
Since American computer scientist Fernando José Corbató created the first password-based authentication in the 1960s, passwords have been an integral part of IT security all over the world. But while the principle of using a string of characters unknown to others remains the same, the world of computing has become exponentially more complex, where an average person now has 168 passwords out of which 87 are business-related.
This causes headaches not only for average users but also for IT admins who handle the secure authentication needs of hundreds if not thousands of employees within their companies who work with a number of applications and devices.
As a global leader in cybersecurity, ESET knows that businesses not only need reliable defenses against malware but also easy-to-use platforms helping them manage daily tasks including secure authentication.
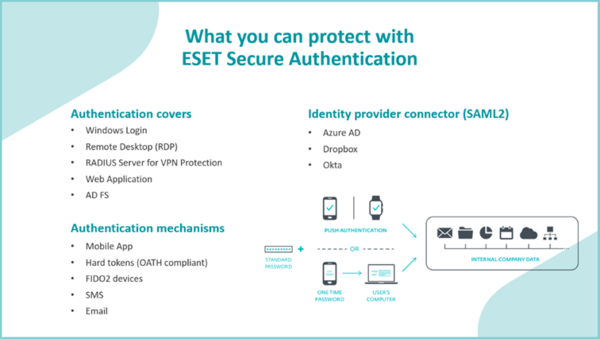
To ease the authentication burden on IT admins, ESET has introduced ESET Secure Authentication, a cloud-based solution running on a single dashboard, that provides multifactor authentication for multiple applications.
Beloved targets
Credentials are among cybercriminals’ most beloved attack vectors. According to the Verizon 2024 Data Breach Investigations Report, 77% of basic web Application Attacks involved stolen credentials, 21% of them were the result of brute force (usually easily guessable passwords), and 13% of those attacks exploited vulnerabilities.
The authors of this report also highlighted the fact that over the past 10 years, stolen credentials have appeared in almost one-third (31%) of all analyzed breaches, making credentials a core component of compromising organizations.
Globally, over 80% of respondents experienced a cyber breach due to authentication vulnerabilities in 2023, and consequences could be detrimental.
In 2023, the FBI received 7,333 complaints about personal data breaches involving a leak or the abuse of personal data. The cumulative loss of these breaches reached over $109,000,000.
There is no surprise that the importance of password security is widely recognized and can be seen, for example, among polled small and medium-sized businesses (SMEs) in the U.S., U.K., and France in JumpCloud’s 2023 Flexibility and Ingenuity Survey. The survey shows that 64% of SMEs use an organization-wide password management tool or software, and 10% plan to implement one this year. For those who don’t use password management, cost is the biggest factor.
When a security practice becomes an attack vector
But there’s also another aspect to password security. Having a robust cybersecurity solution including multi-factor authentication (MFA) is great, but at the same time, it creates new challenges for both users and IT admins.
The problem among users is that they can become so irritated by repeating MFA authentication requests that they lose their vigilance. And there are already cases of MFA fatigue attacks proving that.
At the beginning of an MFA fatigue attack or an MFA bombing, attackers need to obtain targets’ credentials via phishing, brute force, password spraying, etc. Once the targets’ credentials are stolen, attackers start to bombard them with 2FA push notifications in the hope that they will click on “accept,” and thus authorize the attackers’ login attempts, at least once.
On the other hand, IT admins, already struggling with portal and alert fatigue, have gained new responsibilities related to MFA system administration, such as update or alert management.
That is why, for example, the Canadian Centre for Cyber Security advises balancing overall user experience and security protection to maximize security and minimize disruptions.
Here are some other pieces of advice on improving user experience and reducing the burden on IT resources:
- Run both an awareness campaign and training to educate users.
- Allow users the flexibility to use different types of factors, where possible, such as security keys, biometrics, or PIN.
- Give users the possibility to provide feedback on their MFA experience.
- Implement MFA with a single sign-on (SSO) application to automatically log authorized users in to their connected accounts.
- Provide users with a backup MFA factor and set up an easy way to reset them on their own in case their primary factor is lost, unavailable, or compromised.
- Monitor MFA events and check authentication reports to detect anomalous login activities.
- Allow users the ability to disassociate a lost or stolen device/security key from their account.
An end to hard times
Because users often struggle with distributed authentication, split between services, and endpoint, IT admins have a hard time maintaining and upgrading such infrastructure. ESET Secure Authentication aims to take those responsibilities from users’ hands:
- With ESET Secure Authentication, ESET oversees maintenance and upgrading, keeping them scalable, and hunting vulnerabilities.
- The new dashboard shows admins how many users are protected and unprotected, any failed logins, etc. so they can see gray areas that can be improved.
- Admins don’t need to create business invitation cards. They just create an installer, grab it, install it on users’ devices, and enroll them.
- Authentication solutions from other vendors are supported.
Less maintenance, more protection
Secure authentication is a vital aspect of cybersecurity but can also easily get on one’s nerves. Repeated authentication, changing passwords, and doing it on several applications can lead to users’ MFA fatigue and simultaneously drain the IT staff administrating it.
And it’s not only about keeping users and IT admins happy but also securing businesses that can be endangered by FMA fatigue.
With ESET Secure Authentication, businesses can increase automation and reduce maintenance duties for IT admins, thus increasing their resilience against credential-based attacks.