Lately, there has been a lot of discussion surrounding elevated security methods, those that can enhance the way security operators protect their employers and, in turn, create fewer headaches for Chief Information Security Officers (CISOs) in the long term.
As presented by James Rodewald, Security Monitoring Analyst from ESET at the ESET World 2024 session titled “Tomorrow’s Threats Require Modern Prevention with ESET MDR,” modern business security needs go beyond traditional endpoint security, requiring a more sophisticated way to tackle threats, such as with a service that can serve even the most demanding security environments in the form of managed detection and response (MDR).
A challenging security landscape
Mr. Rodewald detailed several challenges that organizations face these days, such as a complex landscape with thousands of attacks each day, with increased business spending driven by compliance requirements as well as demanding salaries for professionals (who are in shortage).
And compliance is a huge challenge. Whether it’s government requirements or cyber insurance, endpoint detection and response (EDR) and MDR are quickly becoming a typical requirement. With EDR becoming more popular, the demand for employees who can monitor the EDR is growing, leading to talent shortages and costlier professionals.
On that note, Mr. Rodewald pointed out that during several of the years he spent interviewing professionals, 49% admitted to gaps in knowledge. Hence, finding and training teams to identify and respond to threats can be difficult, as knowledge gaps can vary.
As an example, he explained that usually, Security Operations Center (SOC) analysts have a heavy focus on phishing emails and have trouble knowing what the behavior of a webshell on an endpoint would look like. If you show them a process tree, of a web server starting PowerShell, an SOC analyst might think, “The user must have opened a phishing email,” which is wrong, as it is an exploited web server. If you don’t have someone who can understand what an EDR is showing you, then they won’t know how to respond when an incident occurs.
At ESET, we have talked at length about challenges faced by small and medium-sized businesses, challenges that they share with large enterprises. This is especially true since malicious actors find smaller businesses as meatier, easier targets, all thanks to fewer resources going into their cybersecurity protection (due to budgetary constraints, for example).
However, enterprises need to worry as well, since thanks to the nature of their supply chains, all it takes is one service/partner to experience a compromise and they can fall like a house of cards as well, as has been the case with several major supply-chain attacks in recent years.
As discussed during Mr. Rodewald’s presentation, these challenges all underline why organizations will increasingly rely on MDR services to enhance their internal security capabilities and better protect against evolving cyber threats.
The ESET power
During the presentation, Mr. Rodewald described how ESET MDR solves the top challenges faced by organizations and how it ensures that users can remain protected, with experts monitoring and instantly responding to malicious activity on endpoints and servers.
Since employee value is crucial today, relying on a team of experts servicing MDR can be very cost-effective, saving resources and time for any business seeking to upgrade its security. The high cost of data breaches leads to customers wanting to have cyber insurance coverage, which MDR can help with, but it can also help with special regulations for verticals such as government, education, manufacturing, healthcare, energy, and utilities.
James Rodewald, Security Monitoring Analyst, ESET
Mr. Rodewald highlighted several reasons why ESET MDR is so unique:
- Reduce your time to detect and respond to a threat from months to 20 minutes with ESET. This makes ESET MDR one of the fastest MDR services on the planet.
- Get unique cybersecurity expertise from ESET, which is part of the Joint Cyber Defense Collaborative (JCDC) and cooperates with other renowned authorities. Our experts operate in 13 R&D centers and have a recognized 35+ years’ track record.
- 24/7 MDR utilizing SIEM and SOAR to provide unmatched high-quality but affordable service even for small and medium-sized businesses.
- Local language support in each service region.
- ESET has its own telemetry and global threat intelligence leveraging 100M+ sensors. ESET leverages telemetry and global unique coverage, gathering unique data about attacks and techniques from the entire world and offers special insight into often under-researched regions and locales.
BLOCK. STOP. DISRUPT.
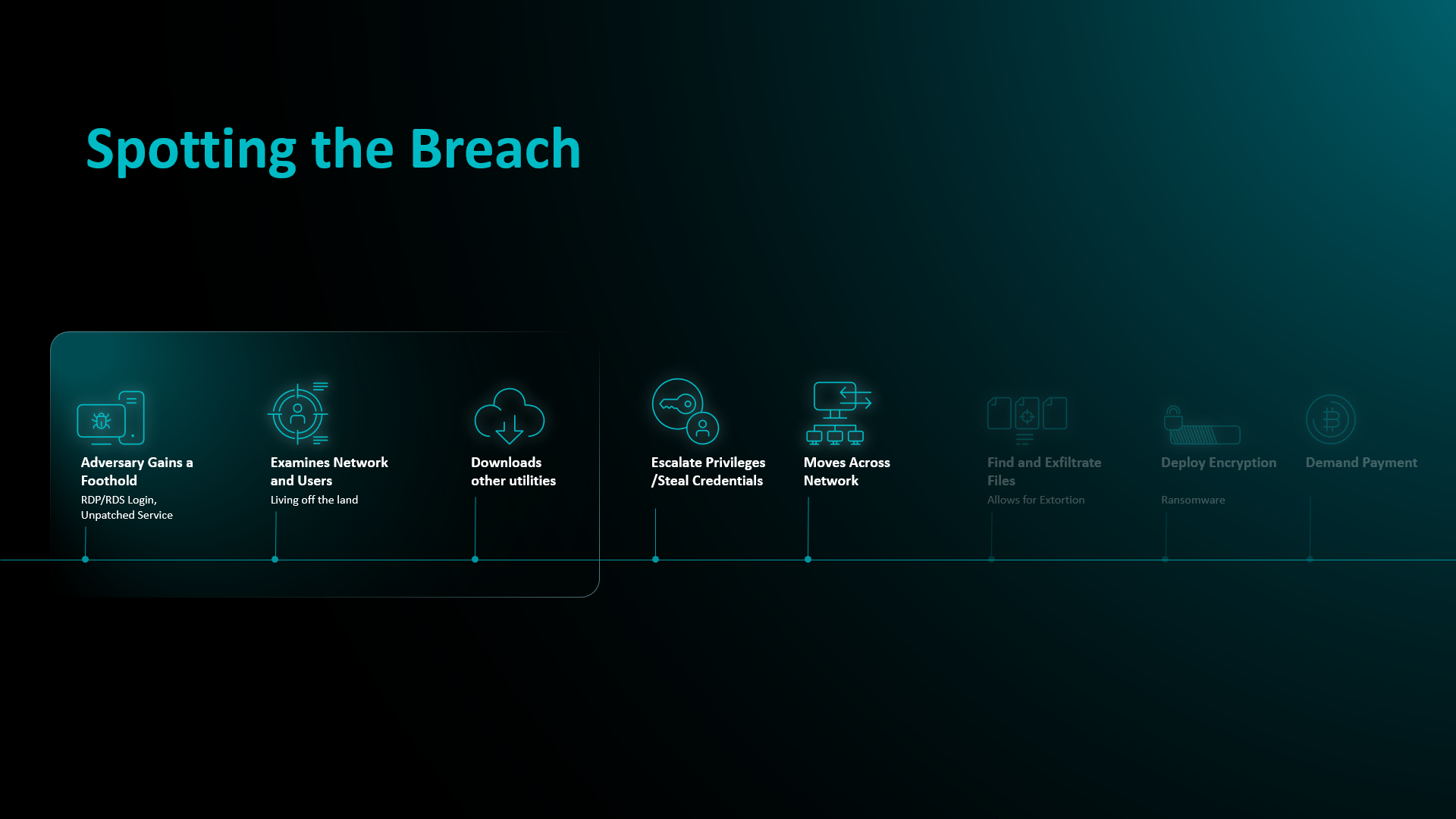
To further prove his point, Mr. Rodewald demonstrated and explained how modern ransomware works, as unlike the traditional notions of it infecting devices through malicious emails or downloaded files, the reality is quite different these days since those types of malware are easily detected.
Compared with the past, common entry points are via remote desktop protocol, MS SQL, or other unpatched services, with threat actors not even needing malware to perform initial discovery of users and computers on a network, since they are already in, abusing admin accounts (often via misconfigured services). They might then download other utilities, including legitimate software (AnyDesk, Megasync, etc.) to help them with their tasks.
This is where ESET MDR can slot in though, as what follows can vary widely, with the actors trying to move across the network to improve their visibility (to domain controllers, for example) and search and collect important files, which are then exfiltrated using the tools they might have downloaded beforehand. Lastly, they encrypt the remaining data/devices and demand a ransom payment to decrypt. Alternatively, extortionware threatens to release sensitive data unless there is a payment, without encryption.
How does ESET MDR mitigate here? Simply put, it will be spotting and stopping the breach before damage occurs, like the exfiltration of files or deployment of encryption; hence, this is why successfully preventing ransomware means that a business will not know if it was a ransomware attack at all.
How long can it take for a breach to turn into ransomware/extortionware? Mr. Rodewald has seen that it takes as little as 48 hours. This is because if no one is monitoring detected threats or EDR alerts, a breach will continue to progress toward ransomware/extortionware. And while the EDR and/or endpoint protection will slow the breach down by blocking some detections, the adversary will just adjust and find a way to circumvent this (change of tactics/tools, work toward disabling endpoint security, or move laterally to an unprotected device).
Each time Mr. Rodewald saw these things happen, he could only think, “If we had had this customer on MDR, this would have been prevented.”
Business challenges addressed
In essence, ESET MDR mitigates cybersecurity skill gaps, eliminates bottlenecks, prevents complex threats like modern ransomware, onboards complex security operations, and helps achieve mature security readiness.
Ultimately, security has to be a top priority for businesses of all sizes, and understanding the level of protection an organization requires is the first step toward a comprehensive security posture to tackle modern threats and the constraints businesses face, especially when it comes to security decision-making.