The philosophy behind firewalls
Around 12,000 years ago, humans abandoned nomadic hunter-gatherer life and settled down to became farmers, building settlements and storing food for the leaner months. Other humans thought this was a great idea: it was easier to steal that food (and other belongings, too) than grow it themselves. It became necessary to build defenses around one’s settlement to protect these things and the people that they supported.
And so it was, much later, with the early internet.
Firewalls are older than the World Wide Web, and they’ve helped secure computers and networks since for around four decades. The firewall remains one of the most recognizable features of network security today. We’re going to look at what firewalls are, how they work, and how the core technology has changed over time.
Firewalls are a cyber security fundamental
At their most basic level, firewalls inspect and filter data to control what flows in and out of an organization’s environment. In the physical world, a firewall serves to partition one area from another: when you climb into a car, there’s a firewall between you and the engine. This keeps the engine (and spilt fuel, flames and so on) from sharing the same space as the passengers in the event of something going wrong.
Getting back to the network world, a firewall, when set up correctly, will permit legitimate uses of the network while blocking malicious attacks and intrusions. What started out as some fairly basic controls has changed over time to a far more sophisticated tool for protecting organizations and infrastructure.
Firewall definition
In a sentence (and all credit here to Keith Ingham and Stephanie Forest): Firewalls are network devices that help to enforce an organization’s security policy.
In cybersecurity, a Firewall is a system - either a device or application - that separates a trusted environment from an untrusted network. Often, this involves evaluating the connection using a series of rules and controls that are set by the organization that controls the firewall. Employed correctly, a firewall should stop unauthorized entities from making connections they shouldn’t in the environment – network, computer, or application – that the firewall protects.
Two types of firewalls explained
There are two general types of firewalls. Network based firewalls sit between one network and another – or several others. In most cases, firewalls sit between an organization’s own internal network and the internet, but in more complex or security-conscious organizations, there may be firewalls between individual internal networks.
The second type is host-based firewalls; these exist directly on a host – such as a PC or server – and serve to either control traffic with the wider network, or specific computing resources.
Firewalls come in all shapes and sizes
In real terms, a firewall can be a hardware appliance that fits into a server rack, a virtual appliance in a virtualized environment, or a piece of software running on a general purpose hardware device such as a PC, server, or router. All of these fit into the first category. Host based firewalls, on the other hand, are a dedicated application, daemon, process, or service that runs on the host. As an example, macOS has its own firewall that can be configured and switched on or off via the System Settings panel.
Firewall use cases
As firewalls have a broad scope, they fit into multiple use cases. We’ve talked about protecting the perimeter, in much the same way as a fortified wall protects a settlement, but firewalls have other approaches and use cases are equally valuable to organizations.
One highly effective use is network segmentation, which both protects sensitive parts of an organization’s environment from data loss and reduces the capacity for lateral movement, should an attacker gain network access by blocking unlimited access between parts of the network.
Another important use is compliance. Regulations such as PCI DSS require the secure storage, processing, and handling of payment card and cardholder data. Some industries and sectors carry significant data security requirements; with healthcare, financial services, government, and defense being among them. If your organization is certified as ISO 27002 compliant, then it will have met specific requirements for firewalling of data, too.
A short history of firewalls
The earliest use of the term firewall in computing coincided with one of the earliest films about hacking: in 1983, WarGames first used the word ‘firewall’ in connection with computing in popular culture, and Steve Bellovin at AT&T Labs Research is credited with first coming up with the term in computing when working with Bill Cheswick on early packet filtering techniques – although both deny being the inventors. Attribution for the invention of firewalls is challenging, to say the least.
But by the time WarGames was released in 1983, the early routers used to build the initial networks that became the internet were already performing early firewall-like activity by basically doing the things routers are intended to do: segregating and managing network traffic.
Firewall types and firewall evolution
Over the last 40 years, firewall technology has been improved, refined, and broadened. Modern firewalls often do far more than the nametag suggests. But it’s worth noting that development hasn’t necessarily been a case of linear progression. As different techniques, approaches, and technologies leapfrogged each other, different types of firewalls appeared, and those have been updated as new requirements emerged. Early firewalls had no way of inspecting the contents of packets, verifying entity’s identities or, for that matter, the ability to handle web applications. New capabilities such as machine learning, deep packet inspection, or the ability to handle traffic to and from IoT (Internet of Things) devices have all pushed and pulled firewall development in different directions at different times.
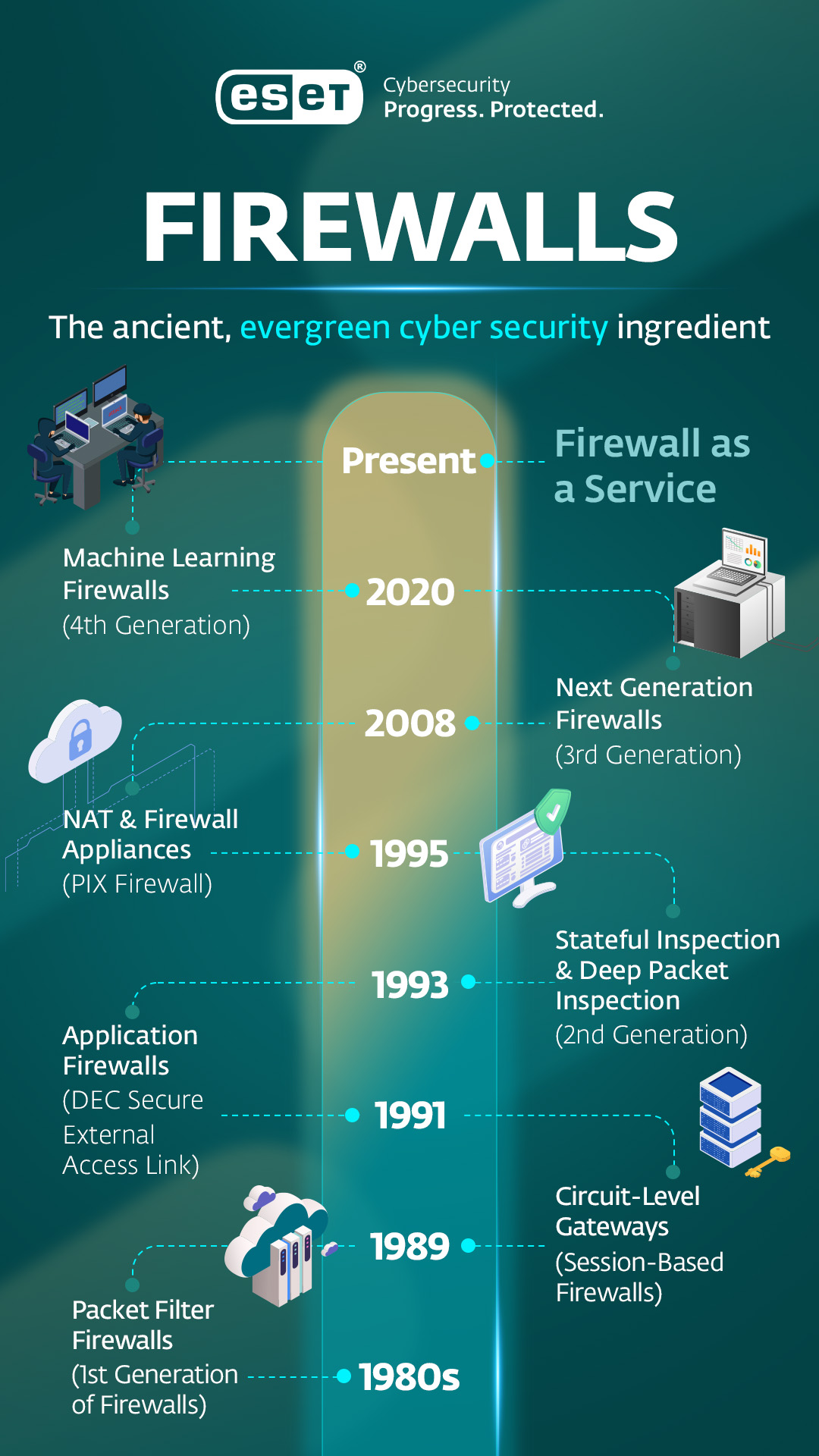
The very first firewalls: Packet filters
Packet filter firewalls do exactly what the name says: they checked incoming packets against an access control list and filtered out the traffic that wasn’t on the list. Arguably, this is the first distinct firewall.
1989: Circuit level gateways and session-based firewall fundamentals
AT&T Bell Labs researchers built what they described as circuit level gateways in 1989 and 1990. Nowadays, with analog circuit switched telecoms networks almost at the point of global extinction, this would be more easily recognized as a session-based firewall. Sitting at the Session layer (Layer 5) of the OSI Network model between the Application and Transport layers (OSI Layers 7 and 4 respectively), these new firewalls built on the basic packet filter to add the ability for the firewall to store and recall how two endpoints talked to each other in the form of tracking exchanges between two IP addresses at the transport layer of the OSI model. A big weakness of these early session-based firewalls was that attackers could simply route their malicious traffic through commonly used TCP ports used by web and DNS services. Ports 6667, used by internet relay chat (IRC), and 8080, often used for unencrypted web traffic, were two particular favorites.
Application firewalls
In 1991, researchers at Digital Equipment Corporation began putting together the first application firewall – DEC SEAL (Secure External Access Link). A step up from circuit level gateways, SEAL and the application firewalls that followed it sit at Layer 7 – the application layer in the OSI model. Identifying unwanted applications or services in applications and in protocols – including Domain Name Systems (DNS), File Transfer Protocol (FTP) and even good old HTTP itself.
1993: The second generation – Stateful Inspection and Deep Packet Inspection firewalls
Gil Shwed and Nir Zuk at Check Point introduced the world to stateful inspection with Firewall-1 in 1993. Functioning as a network based firewall, stateful inspection firewalls scrutinize network connections at the network protocol level. Also referred to as dynamic packet forwarding, second generation firewalls tracked connection for the duration of the session, delivered improved logging capabilities, and analyzed traffic in context. Where previous approaches had looked at data packets as independent items, stateful inspection operated on the basis that most traffic is a stream of packets rather than a single packet, and also often part of a more complex exchange between different entities. Understanding this context granted a better understanding of which traffic might be riskier than others.
Stateful Inspection firewalls were the gold standard for many years, but they did have a number of drawbacks, not least the amount of effort, experience, and knowledge needed to keep them configured properly.
1995: IPv4 extinction, firewall appliances and NAT
It soon became clear that two things were going to become an issue: more people accessing what were primarily government and academic networks meant more mischief and mistakes, and the number of available IPv4 was due to run out soon. This led to the segmenting of IPv4’s network address space into blocks of public IP addresses accessible to anyone, and private IP address spaces reserved for use solely as internal networks that were not accessible from the public internet. It’s worth noting that we’ve now been running out of IPv4 addresses for about 30 years, by the way.
In 1995, Network Translation, Inc, introduced the PIX firewall, aiming to address the twin challenges of IPv4 address depletion with Network Address Translation (NAT) between public and private IP address spaces and the need for a commercial firewall appliance. The product was so successful that Cisco acquired the business a few months later.
2008: Next Generation Firewalls (NGFW)
The next step (taken by Palo Alto Networks, in this case) was to look at the full network stack, build in intrusion prevention systems, and look at traffic from the perspective of users, applications, and content.
This third generation – popularized as the Next Generation Firewall (NGFW) by Gartner in 2004 and picked up, productized, and popularized as a term by Palo Alto Networks, was in response to increasingly diverse network traffic and increasingly complex threats. NGFW augmented basic firewall functionality, adding Deep Packet Inspection (DPI) and Intrusion Prevention Systems (IPS). Other existing technologies such as bandwidth management, AV inspection, SSL decryption, and identity management were also folded in.
Peer to Peer networks push Firewall evolution
These new developments addressed a significant challenge that traditional firewalls had first bumped into during the boom in Peer-to-Peer (P2P) file sharing services such as Napster and LimeWire: administrators were able to filter out connections to these two services based on the TCP/IP ports they used to access the internet, but users could bypass this control with ease, simply by changing the TCP/IP port number to something their organization’s network typically used for web traffic.
NGFW quickly became the standard for enterprise and large organization security, and refinements to the basic premise continue to this day.
2020: The next (next) generation: powered by Machine Learning
It’s easy to forget in these days of AI-powered everything that the hot new term just five years ago was Machine Learning (ML), but ML has been responsible for significant leaps in cyber security capability across the board.
Machine learning led to the Fourth Generation of firewalls, capable of doing two things its predecessors could not: act proactively and make inferences on data to identify potentially malicious activity. This generation of firewalls makes use of machine learning’s pattern-recognition capabilities to look for traffic patterns that may signal an attack. While previous rules-based firewalls required known threat signatures to identify threats or set boundaries for what administrators considered ‘safe’ behavior and traffic, Fourth Generation firewalls could identify and act on suspicious traffic and behavior proactively.
MSSPs and the firewall as a service
With the advent of Managed Security Service Providers (MSSPs) bringing increasingly sophisticated and resource-hungry services and tools to smaller businesses, firewalls have undergone a further change from appliance or application to a service delivered from the cloud. Aside from the ability to bring sophisticated and expensive capabilities to smaller organizations or those with severely constrained budgets or staff, cloud based firewalls also provide flexible and powerful capability for very large or fragmented organizations.
Future trends and directions in firewall technology
Several factors, technologies, and trends will affect what future firewalls look like and how they protect organizations. It’s likely that, as with many other areas, AI will start to have an impact.
One of the major vendors, Cisco, is already working with a consultancy to integrate some form of AI into the provisioning of its firewalls Machine Learning, an AI technology has already proven effective in cyber security for years, of course. The ability of Machine Learning and Artificial Intelligence to pick up signals and patterns that may indicate malicious activity and suggest rules and countermeasures makes this area both exciting and potentially rewarding for defenders.
As we’ll find out, automation and scaling is also a challenge for organizations having to manage large numbers of firewalls, and the use of AI to automate some processes is also potentially useful.
Cloud-native and SASE models acknowledge the massive long term impact of Cloud infrastructure and the need to ensure consistent security across dispersed and diverse environments.
Zero Trust will undoubtedly have an impact on firewall strategies one way or another; shifting the security approach to perimeter defense to continuous verification at every endpoint, application, and network segment won’t be the death knell for firewalls, but it certainly will add to both the capability and complexity of security set-ups.
Transport Layer Security inspection
One final and slightly controversial area of change will likely be the increasing use of TLS (Transport Layer Security) inspection. This routes internet (and other) encrypted traffic into and out of an organization’s network via a web proxy operated by the organization that uses a wildcard digital certificate to decode HTTPS and other encrypted sessions between the organization’s users and entities, and internet-based resources. This helps counter an increasing use of HTTPS and other encryption by attackers to disguise malicious activity and content – but it also means employees’ confidential communication is potentially exposed. For better-resourced organizations, TLS inspection can take place on-premises.
The current state of firewalls: still indispensable, and proving its worth every day
Modern firewalls are effective, robust and come packed with capabilities and features that make them an invaluable tool for organizations to secure their data and protect their people. But they’re not perfect.
There’s a catch: modern firewalls are complex beasts, and it’s understandable that this can lead to them being overly complex, poorly configured, and packed with redundant rules and features. A survey by firewall analytics specialist and policy management firm FireMon noted that 30% of firewall rules are completely unused, and 10% of rules are either redundant or shadowed. The fallout of this and other challenges: 60% of the firewalls FireMon surveyed failed high severity compliance checks – 34% of which were of critical severity.
Real world examples that prove the value of firewalls
A real world example of configuration error was the 2019 CapitalOne breach, which saw the theft of more than 100 million consumer credit records from the bank due to a misconfigured Web Application Firewall (WAF) used by the bank. WAFs have secured web applications since the mid-2000s, principally to protect against Cross Site Scripting (XSS) and SQL injection attacks. An Amazon employee was ultimately convicted for the breach, which affected 30 institutions and cost CapitalOne $270 million in fines and compensation payments.
It is most definitely worth holding in mind the PPT acronym: People, Process, Technology. The latest and greatest new generation of firewall technology is always around the corner – and rarely fails to impress – but it is meaningless without the right people to configure and maintain it, and the right procedures to make sure it does the job.
If you’re looking for an example of how good firewall practice makes all the difference, then the WannaCry attack in 2017 is an excellent case study. Aside from the ingenious hack to neutralize WannaCry executed by Marcus Hutchins, another defense went unnoticed. Reconfiguring the humble Windows firewall on Windows devices to block connections on Port 445 from the internet also foiled WannaCry’s initial method of attack.
Firewalls: The Ever-Present Backbone of Modern Perimeter Defense
Firewalls will remain a cybersecurity constant for the foreseeable future, but it’s clear that firewalls are a part of the perimeter defense strategy used by organizations. It’s also the case that firewall capability is a powerful ingredient in a huge variety of different hardware, software, service, and cloud products, from tiny IoT devices up to hyperscale cloud services.




