In recent years, a significant number of cyberattacks have been ransomware related and, despite fluctuations in frequency and intensity, they remain one of the most prevalent and feared security threats, which only a proper prevention-first mindset enabled by the right decision-supporting tools like threat intelligence can stop from disrupting a business’s operation.
Key points of this article:
- ESET Research’s discovery of the AI-powered PromptLock ransomware highlights a growing sophistication of malware potentially in use by threat actors.
- Defenders are left to enact protection based on a keen understanding of their exposure to cyberthreats, for which threat intelligence is a powerful supporting tool.
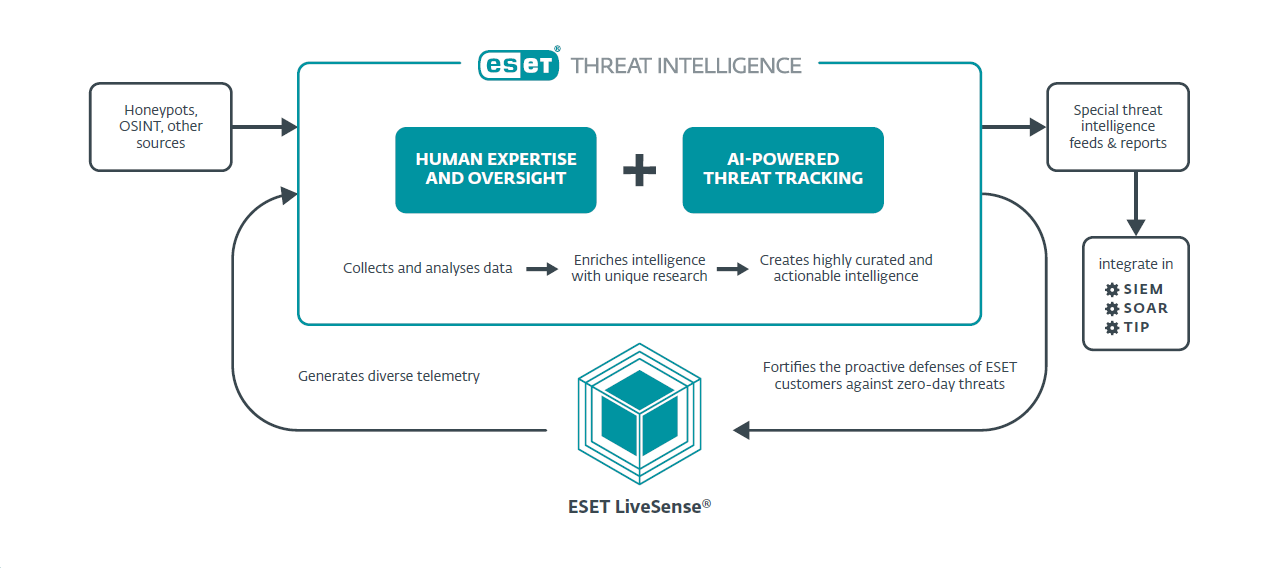
- ESET Threat Intelligence (ETI) presents highly accurate, curated, and actionable feeds. ETI clusters data on a wide spectrum of malware, finds similarities or particularities, highlights what stands out, and monitors attack chains and any changes in TTPs.
- This automation occurs in real time, providing end customers with the most actionable intel on threats targeting them.
- ESET Threat Intelligence provides its data feeds to customers through the TAXII server in the most widely used formats, such as JSON and STIX 2.1 for use in the most popular intelligence platforms.
- Researchers, SOC teams, threat hunters, and more can benefit from the beneficial aspects of threat intelligence, leading to a proactive prevention-first security strategy.
Human-powered
Ransomware attacks are highly orchestrated, but what makes them particularly insidious is that they are not merely automated programs running rampant through systems without direction — they’re often controlled minute-by-minute by human attackers, usually beginning as directed spearphishing attacks against high-value targets. That said, with the help of generative AI, these phishing attacks have quickly become vastly more potent.
While these campaigns still require human intervention and ingenuity to run, long-held fears over AI-powered ransomware have recently been realized following ESET’s discovery of the PromptLock ransomware, which uses the gpt-oss:20b model from OpenAI locally via the Ollama API to generate malicious Lua scripts.
This AI-powered ransomware can exfiltrate, encrypt, and possibly even destroy data, though this last functionality appears not to have been implemented in the malware yet. While PromptLock was not spotted in actual attacks and is instead thought to be a proof-of-concept (PoC) or a work in progress, ESET's discovery shows how malicious use of publicly available AI tools could supercharge ransomware and other pervasive cyberthreats.
Tactics, techniques and procedures
Via the many tactics, techniques, and procedures (TTPs) attackers use to deploy the necessary tools they may use, whether via AI or traditional methods, the goal remains the same: to meticulously navigate dozens of steps in search of valuable information within the compromised network.
Once this occurs, the options left to defenders narrow, moving from defense to measures focused on mitigation — or worse, remediation.
Furthermore, the selection of “measures” is very much based on a keen understanding of the threats faced and any associated peculiarities, whether they be unique processes around privilege escalation or credential access techniques that enable cybercriminals to retrieve sensitive information until they can exfiltrate what they deem valuable.
To counter all this, ESET Threat Intelligence (ETI) processes hundreds of millions of indicators of compromise (IOCs) daily; this is akin to building a new database of clues left by cyber-intruders while they crawl through a victim’s network.
Putting threat intelligence to work
Researchers, SOC teams, threat hunters, and even curious prevention-minded IT admins can benefit from the multiple aspects of threat intelligence that inform everything from replicated attack scenarios that aid red and blue team network defenders, to security strategies, extended prevention measures, digital forensic incident response (DFIR), and virtually the entire incident-response lifecycle.
ESET Threat Intelligence comes to users in highly accurate, curated, and actionable formats that enable customers to logically pursue a prevention-first approach to security. Specifically, both (wider) industry and ESET Threat Intelligence data are compiled and ready to be paired with observations made via other tools, including XDR, SIEM, and/or SOAR, to prevent damages from (for example) ransomware and any subsequent extortion from taking place.
Users employing data/intel gathered in ETI for their inspection and/or monitoring of security incidents is just one way to create better-informed security operators. In this case, human operators, increasingly supported by automation, might for example more intentionally interact with incidents reported in an XDR’s triage system: executables, malicious processes, computers, and threat indicators.
From there, various forms of mitigation can be conducted in an informed, systematic, and prioritized manner. Specifically, a user might employ ETI to cross-reference relevant data to better understand the actions necessary to perform in an EDR solution like ESET INSPECT (the XDR-enabling module of the ESET PROTECT platform).
Threat Intelligence – the tricks & trade of ransomware
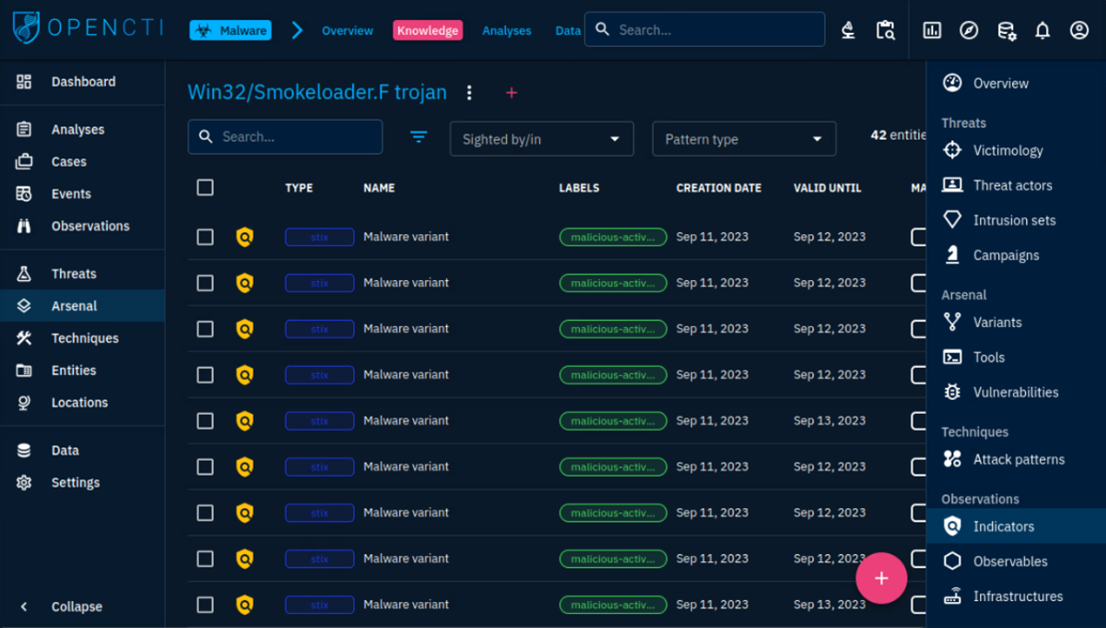
In late 2023, ESET observed the SmokeLoader malware family, a generic backdoor with a range of capabilities that depend on the modules included in any given build of the malware being utilized as one of the multiple variants packed by AceCryptor, a crypto service used worldwide by cybercriminals to obfuscate malware. SmokeLoader is deployed to download and execute the final payload of an attack discreetly, to evade security measures, making it crucial to rely on robust cyber defense mechanisms.
Thankfully, ETI assembles all the clues needed to deploy prevention mechanisms and, when necessary, effectively mitigate against malware like SmokeLoader. Defenders can specifically utilize ETI's backend tracking systems to support an improved understanding of such threats and apply their learnings from ETI’s feeds to support proactive defense processes.
Related (longer) reading: Cyber Threat Intelligence: A Comprehensive Guide to Your Threat Defense

ETI clusters data on a wide spectrum of malware, finds similarities or particularities, highlights what stands out, and monitors attack chains and any changes in TTPs. This automation occurs in real time, continuously updating all feeds to provide end customers with the most important and immediately actionable intel on threats targeting them. These outputs are also synthesized into specific APT reports, which ensure customers receive pertinent information without being overwhelmed by excessive data.
Data aplenty
A much wider spectrum of curious, prevention-minded admins can now turn to the main ESET research findings and other relevant data. These are published in regular reports on the ETI platform and portal and are accessible in specific territories, with ESET continuously working to expand their availability.
ESET Threat Intelligence provides its data feeds to customers through the TAXII server, integrating it directly into their current systems (for example, Microsoft Sentinel or the OpenCTI Threat Intelligence Platform). The feeds cover various aspects of cybersecurity, including tracking malicious files, botnets, and APTs; identifying potentially harmful domains or URLs and IPs considered malicious; and tracking the associated data. To ensure compatibility and easy integration, the feeds are provided in widely used formats, such as JSON and STIX 2.1.
ETI for all
ETI’s benefits are vendor agnostic, so businesses already running alternative SIEM/SOAR products, including Microsoft Sentinel, OpenCTI, IBM QRadar, Anomali, Block APT, Elastic SIEM, and ThreatQuotient (outside of the ESET PROTECT ecosystem) can gain from ETI’s unique data stream via our API.
Fighting malicious activity
Preventing multifaceted threats from impacting your network, business continuity, and/or reputation requires a comprehensive and always up-to-date knowledge base. Thus, moving beyond the technical defenses against ransomware and other malware, security operators at organizations must adopt a knowledge-based security culture that puts learning on level with action.
The cornerstones of security are particularly essential at public and private institutions that depend on well-developed SOC teams, threat hunters, and security operators, who have both technical skills and access to the ever-growing body of work on threat actors, system configuration, and an understanding of what is and isn’t working.
These cornerstones are where ESET Research employs its long history of collaboration with law enforcement agencies, the Joint Cyber Defense Collaborative, and even its work with “No More Ransom” to communicate our views on ransomware, fight threats at large, and inform how and why we’ve built our threat intelligence platform, ETI.
Explore your use case for ETI via ESET API, ESET APT reports, the ETI data feed, or a comprehensive toolset for an ESET-powered prevention-first approach.












