Oftentimes, business leadership struggles to see the value of their security product or service. They think of compromises, breaches, and incidents as demonstrable evidence of threat actors at work and, without which, their service seems kind of “redundant.”
But is it? The devil, as always, is in the details.
Following the sometimes bombastic-sounding stories at ESET World 2025 and ETeC 2024 about what it’s really like to protect complex, often multivendor customer environments, ESET’s resident Senior Security Monitoring Analyst, James Rodewald, and Product Manager Gabriel Balla returned to the 2025 ESET Technology Conference (ETeC) to, once again, set the record straight.
Systems on fire
Mr. Rodewald began his presentation by reminding the audience that having organizations without a security service, often with only one person covering their security with distinct EDR/XDR solutions from multiple vendors, is a very poor choice, considering how complicated incidents can be.

To visualize said point, Rodewald spoke of his encounter with the BlackBasta ransomware in a cat-and-mouse game spanning multiple systems and entry points: “This was a four-day event,” Rodewald began. “The customer’s monitoring, they see everything as fine, until suddenly, everything’s actually on fire.”
Initial access
It all began with a bit of confusion. Rodewald explained that initial access took place in a very peculiar fashion — all it took was the abuse of legitimate remote desktop service (RDS) server tools.
Basically, the victim had an RDS server that was hosting applications. The threat actors logged into its web portal, launched an app, pressed shift five times, clicked the hyperlink, and then started executing commands from the address bar.
“If that doesn’t make sense, that’s fine—I confused the customer too,” Rodewald noted. He then went on to demo the attack.
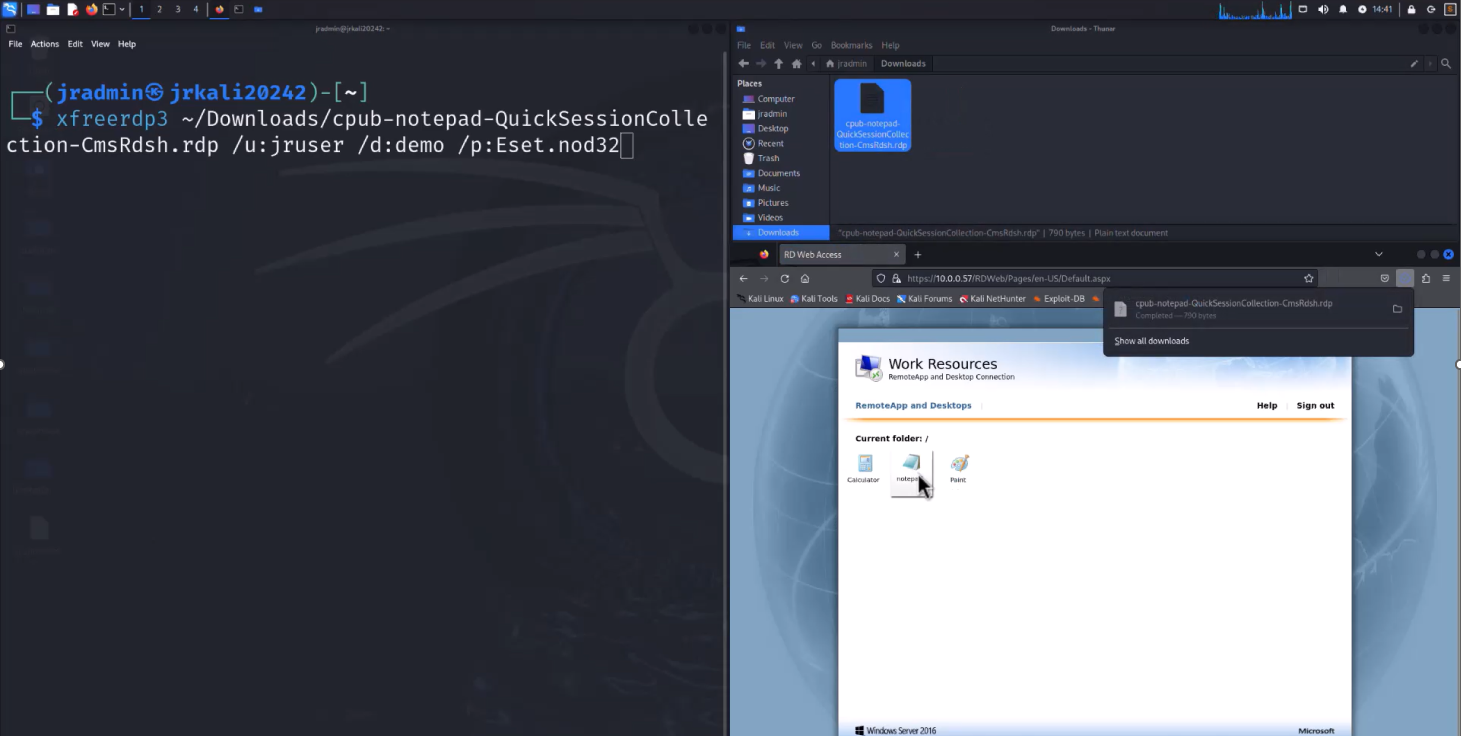
On a Kali Linux box, Rodewald logged on to the company’s RDS server, which presented him with a different app, out of which he picked Notepad, downloaded an RDP file, and used free RDP to connect to it.

“I now have Notepad open on Kali, I press shift five times — we’re all familiar with the sticky keys pop-up — so when I click the hyperlink, it opens the control panel, which has an address bar. I can type in a URL there. It will launch Internet Explorer or MS Edge, and then I can navigate through websites, I can download tools, I can browse the file system of the server — no malware required, this is how RDS servers work,” described Rodewald.

The result: They could launch whatever they wanted. What Rodewald found most interesting about the attack, though, was how for the logon, instead of it being a user, it was RDP itself that was launching Outlook. “They [the attackers] didn’t seem to care about the emails, because they would just launch sticky keys,” Rodewald surmised.
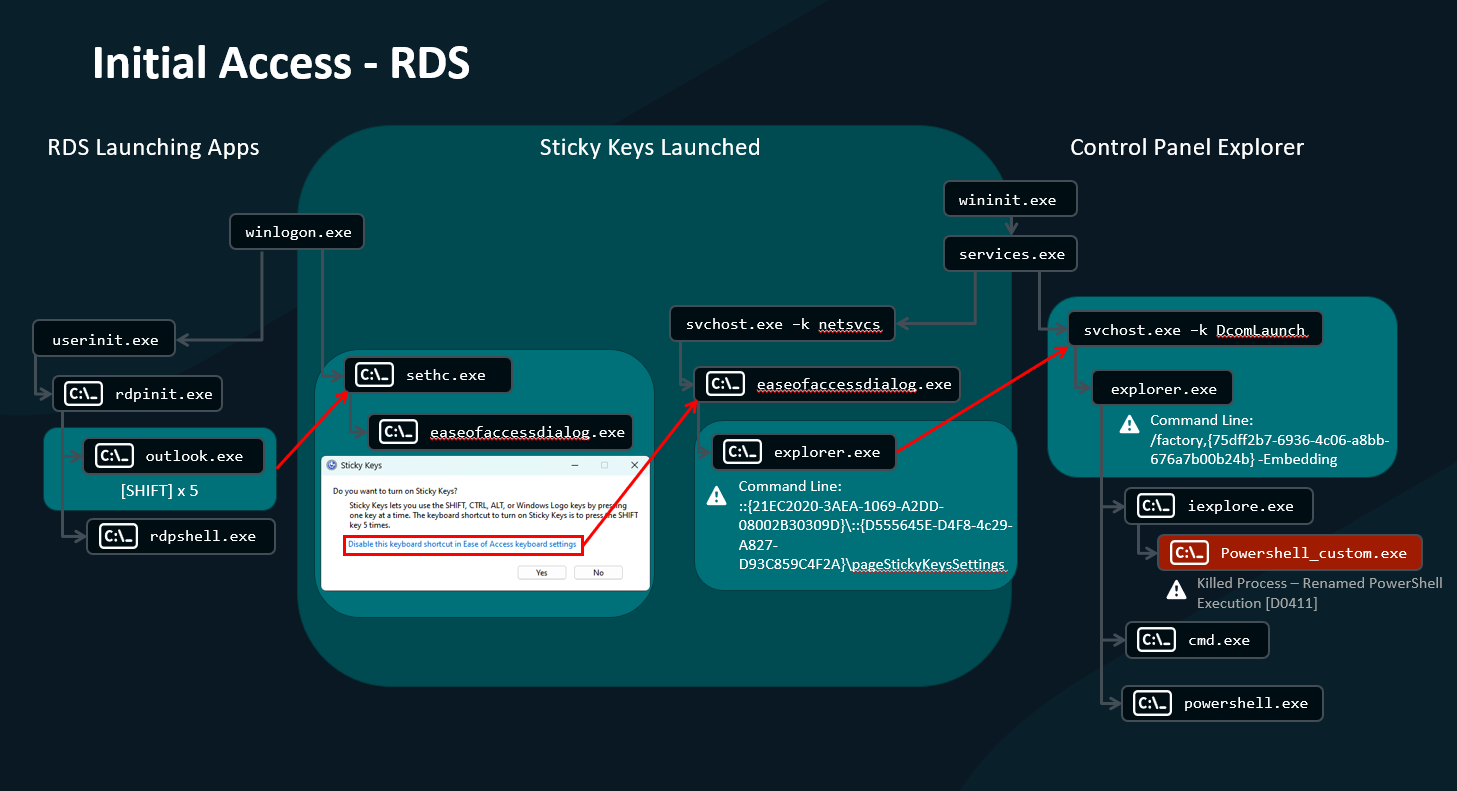
The attack had multiple different process trees, which Rodewald found difficult to map out on his own, but not impossible. He discovered that in the final phase of initial access, the adversary launched Internet Explorer: “The very first thing they did was to download a renamed PowerShell executable and execute it. This was instantly blocked by ESET’s EDR.”
Discovery and living off the land
Initial access was followed by a discovery phase. The attackers employed multiple tactics just to see which systems they were on, followed by a lot of ingress file transfer attempts, using multiple living off the land (LOL) tools to abuse legitimate system services in order to transfer files onto the compromised system.

The adversary was very motivated, an important attribute that should have gotten detected early: “If I break this down just to the detections per day in the first 48 hours, this should have been seen on day one. The now renamed PowerShell was executed 19 times. Day two, tons of hacking utilities like Cobaltstrike and more… This should have never made it past day two,” he warned, saying how with an active MDR service, all this would have been dealt with in minutes.
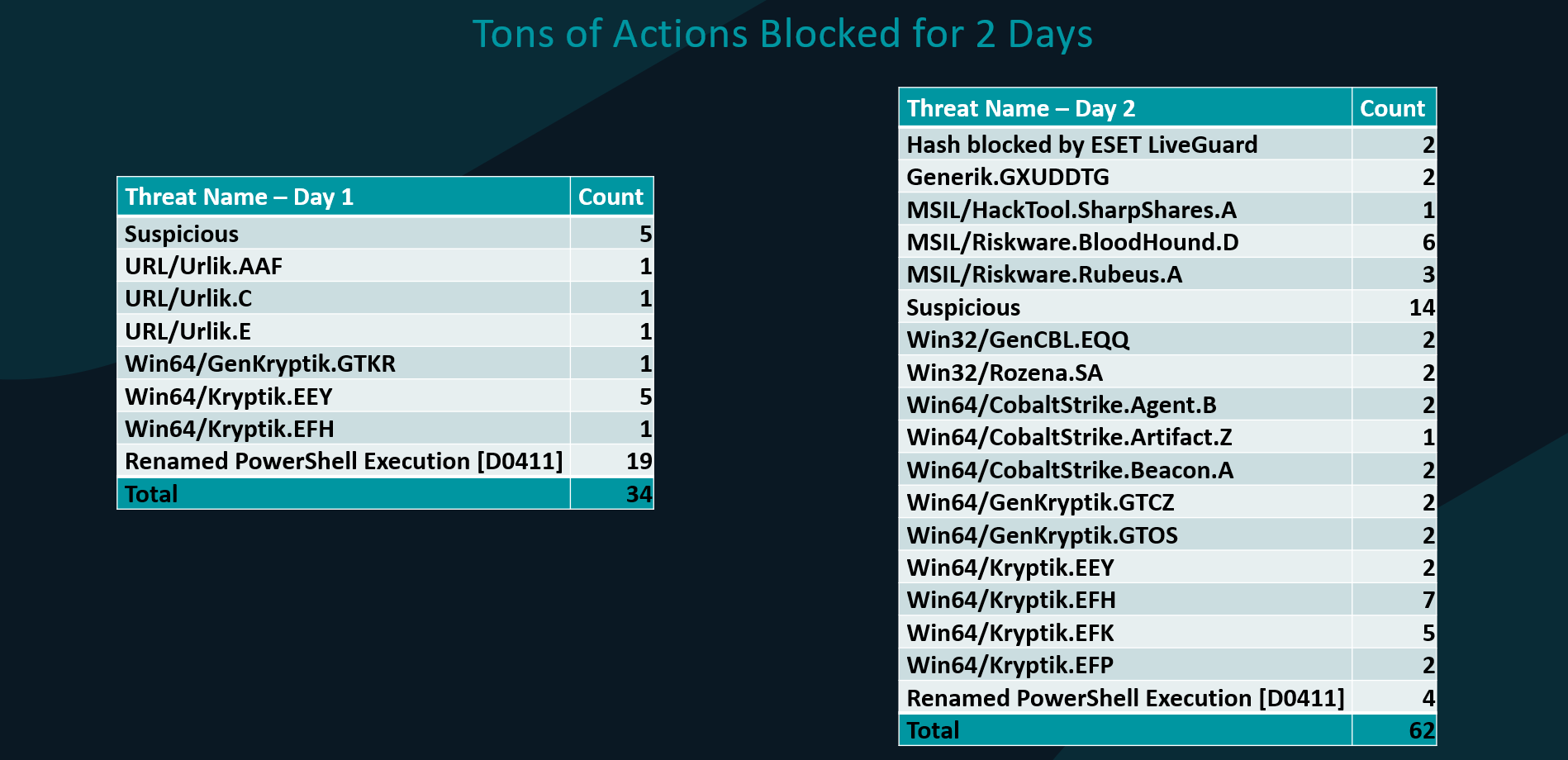
Blocked tools but no fools
So, with one admin monitoring multiple systems through a hybrid security approach — i.e., running several disparate endpoint protection products in parallel — and the attackers being consistently blocked, how did the attackers ultimately execute the ransomware? “They didn’t,” explained Rodewald. “They found a PDF file named ‘Company Passwords.’” Persistence pays off, right?
Essentially, the adversary gave up on the first device they were on (due to their constantly being blocked by the endpoint product), and then moved laterally, using RDP, to an unprotected server and 127.0.0.1. The latter move was very interesting to Rodewald: “If we look back at where I’m in control of the control panel and I launch the RDP client and connect to 127.0.0.1…you would think, ‘Okay, it’s an RDS server. It should not allow this’…but it does.”
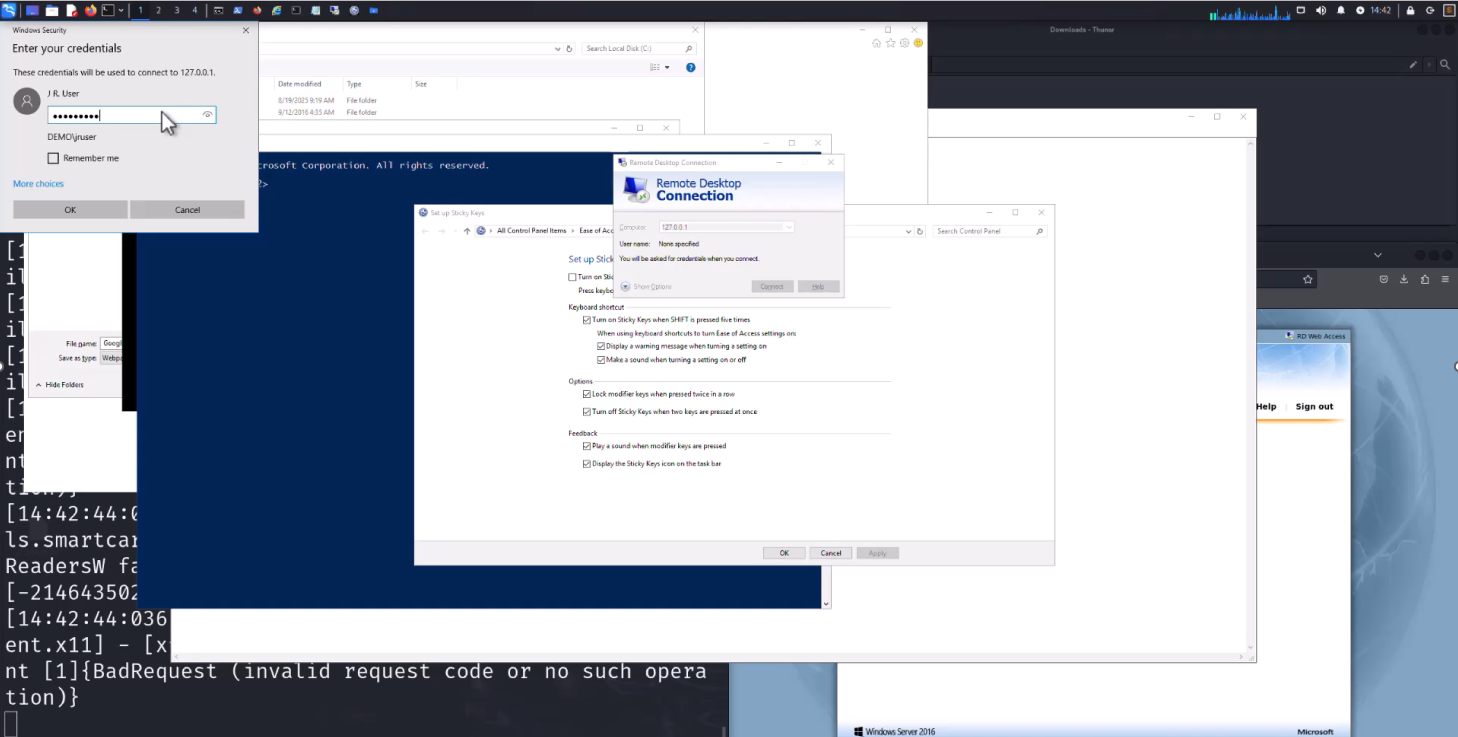
Just as the adversary had, Rodewald demonstrated full control of the entire Windows GUI. Not ideal for the victim, but at this stage, the attackers’ actions were still being automatically blocked: “But they were a smart adversary and knew how to move around a network,” continued Rodewald. “In fact, they’d started adapting to the blocking attempts.”
As the situation escalated, seen in post via ESET Inspect, it became clear from their changed TTPs that the attackers were bringing in progressively more skilled individuals to probe for weaknesses. Rodewald noted, “By day four, the adversary was ready to deploy ransomware following credential theft and lateral movement to the unprotected server.”
Their chosen ransomware was a .dll file to be executed via Rundll32: “So they’re going to copy this .dll to every single device on the network and use wmi to execute a Rundll command,” said Rodewald about the attackers’ next move.
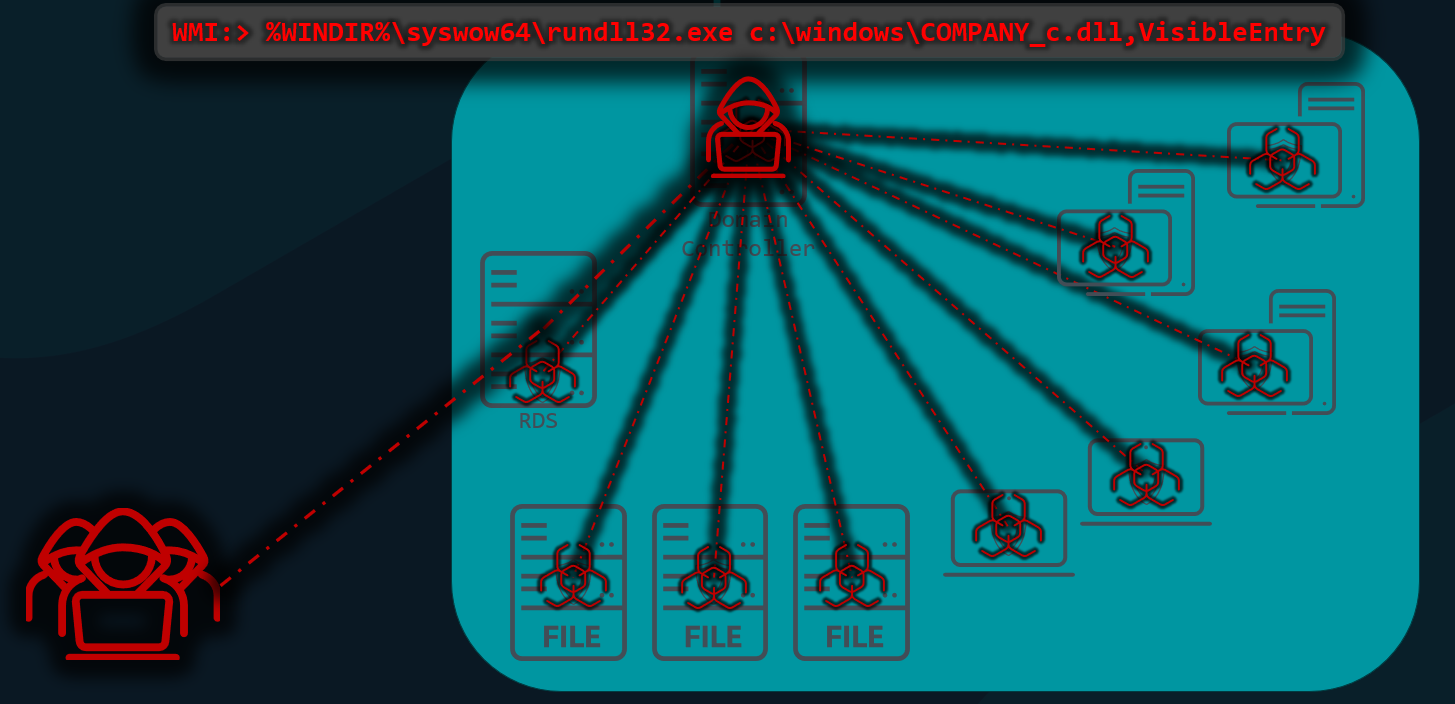
While endpoint security can protect against most attacks, more advanced TTPs can be beyond its capabilities — creating a gray area between endpoint and EDR/XDR protection efforts. Thus, the attackers had struck gold, as this skillfully handcrafted scenario wasn’t detected by standard endpoint security, so they were free to run their encryption scheme in said area due to a lack of an informed observer.
However, what the attackers couldn’t fathom was that their would-be victim had a surprise waiting for them, namely AI behavioral detection enabled by ESET LiveGuard Advanced plus ESET Inspect.
In short, the system recognized that it hadn’t seen that malicious .dll before, and as a result, it knew how to execute it in its sandbox: “Within three minutes, it was able to make a decision that said: ‘Go ahead and remove it from every device on the network that’s protected,’” Rodewald explained.
Nice, right? Ransomware stopped dead in its tracks, all automatically.
Except, the victim still had multiple servers willfully left unprotected: “At this point…had they [victim] had someone who was monitoring with the right skillset, e.g. mature EDR skills, this would have been stopped [two or three days earlier]. The lone admin was basically outnumbered. One person, monitoring an entire network, it’s never gonna conclude successfully,” finished Rodewald.
Final takeaways from James' story

This scenario lays bare the boundary between where largely automated protection from endpoint products begins to wane and the point where threat actors “go custom” and begin to deploy TTPs and handcrafted scenarios.
“It’s a shift from chess to StarCraft,” remarked ESET Product Manager for Business Cloud Solutions Ľudovít Bobula. “The difference in this scenario was that in the customers’ hybrid environment, our standard product stretches its protections further by leveraging Live Guard, and then for the portion of the ESET-protected customer environment, our XDR-enabling ESET Inspect was also active and able to aid in [documenting the TTPs used, stopping the attack].”
Ultimately, customers cherry-picking which system would or wouldn’t be protected and monitored via EDR/MDR, be it deliberately or not, said gray area shouldn’t leave a lot of security gaps for wanton exploitation. A skilled security analyst, or an external MDR service provider, would have pointed this out almost immediately, but sadly, that wasn’t the case here.
MDR in transition
Picking up where Rodewald left off, Gabriel Balla, ESET Product Manager for Business Endpoint Security, stepped in to demonstrate how ESET MDR has evolved to meet threats just like the one we’ve just seen. With deployments in over 40 countries, MDR isn’t just a product — it’s a frontline service that’s constantly studying, adapting, and scaling to meet the needs of real-world defenders.

ESET MDR telemetry trends
So, what do real-world defenders have to contend with? ESET MDR’s (specific) telemetry might shine some light on that. While the second-most detected threat categories were phishing and social engineering (22%), followed by exploitation and lateral movement, Balla explained that ransomware topped all categories (48%), and he expects it to remain relevant, as it’s not just a number; it’s a warning. And it’s why MDR’s rapid response capabilities matter more than ever.

One stat caught even Balla off guard: “72% of incidents happen during work hours,” he said. It might seem counterintuitive, but it makes sense. Attackers want to blend in with legitimate activity, and there’s no better cover than a busy network.
Improvements to ESET MDR
The good news? MDR is getting sharper. Even as incident volumes rise, false positives continue falling — a testament to the tech, but even more so to the people behind it. The same kind of experts who, like Rodewald, can spot a threat hiding in plain sight.
Recent improvements wouldn’t have been possible without some notable changes. Balla explained that one goal within MDR is to keep customers as informed as possible, since transparency is key in maintaining a trusted relationship.
For this reason, ESET MDR has received several improvements:
- Improved notifications with incident overviews and descriptions: “To inform customers about MDR actions as soon as possible,” said Balla.
- Enhanced dashboards and reports for MSPs: “We wanted to enhance MSPs’ user experience,” explained Balla, “so they could more easily understand their clients’ environments.” The reports follow a similar logic, generated for each tenant every month.
- Seamless MDR dashboard details: “Customers don’t need to go into ESET Inspect to see the details of their incidents,” added Balla. “It’s all in our PROTECT console. It’s quite fast, so customers can get every detail more quickly.”
- Critical assets: “Customers can select their most critical endpoints and define what kind of actions the MDR team should or shouldn’t trigger on those endpoints,” said Balla.
Additionally, ESET MDR’s upcoming new Active Incident Support will provide rapid, expert assistance in English for active ongoing security incidents detected through ESET product telemetry. This support enables direct engagement with ESET specialists to help contain threats and minimize potential damage, leveraging available ESET data for swift and effective response.
Problems with low deployment and zero incidents
Balla followed his description of new features by highlighting a big one — low deployment rate notifications.
Simply put, by not enrolling all the endpoints in use under the MDR service, customers can’t expect reliable insight and protection. “We really want to encourage customers to fully utilize their environment. Without complete deployment, we cannot protect them effectively,” explained Balla. As Rodewald’s story made it painfully clear, all it takes is one unprotected server to bring the whole house down.
However, in the face of this reality, Balla has noticed some hesitance regarding low-incident rates. “Currently, some see little value in the existing MDR dashboard because, if there are no incidents, most widgets appear almost useless — they display no activity.”
Having zero incidents is an ideal situation, though — MDR is a “break the glass in case of emergency” sort of service, a safety net that can rapidly respond to severe incidents, to which low-level events can easily turn into.
“MDR matters — especially for customers without skilled security specialists, time, or budget, hence the need of having a managed service. Even if no incident is created, they should still understand what we’re protecting them from on the daily,” commented Balla.
Fires and extinguishers
In the end, the stories shared at ETeC 2025 aren’t just cautionary tales — they’re proof points. Proof that even the most determined adversaries can be outmaneuvered with the right tools, expertise, and visibility.
ESET MDR isn’t just a service; it’s a strategic advantage — one that turns chaos into clarity and panic into prevention. Whether it’s stopping ransomware in its tracks by detecting stealthy lateral movement, or detecting that pesky hacking tool, MDR proves its worth not in the absence of incidents, but in the resilience it builds. Because when the next fire starts — and it will — the question isn’t whether you’ll see it coming or not, but if you’ll have someone ready to put it out.










