ESET Research has revealed a concerning fact — gamers are being targeted by cybercriminals, and it’s no mystery why they are such meaty targets.
The gaming industry is huge — some games generate millions in monthly revenue, satisfying gamers and executives simultaneously. However, in some cases, gaming can present some very real dangers that are a bit more severe than getting a virtual arrow in your knee.
I wanna be, the very best
How far will a person go to excel in their game?
With the advent of online gaming, more and more people are playing together in real-time, leading to more social interactions than ever before. This can lead to a lot of pressure, especially when playing online games with a player vs. player (PVP) aspect like multiplayer shooters or battle arenas.
When you want to be the best, you will focus on improving your skills, right? Well, quite a few people would rather cheat their way to the top of the rankings, raking in the gain without the pain.
Cybercriminals know this, which is why when venturing online, gamers can find a multitude of interesting cheats like wall hacks or aimbots for better visibility and accuracy to help up their game. What they don’t know is that these cheats are often loaded with malware, hence cheating your way to the top can lead to someone else taking a peek at your personal data via infostealers such as RedLine Stealer or Lumma Stealer, which ESET Research’s telemetry confirm as quite active.
What is an infostealer?
An infostealer is a piece of malware that, after infecting your computer, starts exfiltrating (stealing) information from the compromised device. Such data can include credentials saved in browsers, financial information, browser cookies, crypto wallets, or others.
These are often sold as a service, with RedLine Stealer costing just $150 per month. To make matters worse, like home automation software, RedLine works through a simple dashboard, making its deployment to victims hassle-free.
The game has just begun
However, cheats are not the only attack vectors for infostealers to infiltrate your device.
When you really like a game, like Minecraft, for example, you might want to go beyond what the developer offers with the default set of assets and gameplay scenarios. For example, players of the Java version of Minecraft often modify their worlds by adding additional creatures, building blocks, or more ways to use redstone, leading to creations such as functional computers inside the game (the creativity is limitless, really).
While it is great that players seek more creative ways to redefine their game experiences, cybercriminals also abuse this. You see, mods (game modifications) are usually available as downloads —– for Minecraft, typically on web pages like Planet Minecraft or Minecraft Mods. These are all publicly available platforms, hence why cybercriminals try to exploit such places with their nefarious prospecting by updating modifications and injecting them with malicious code. Such was the case reported by Bleeping Computer, when hackers compromised several accounts on modding platforms to distribute infostealers, hijacking existing projects.
Sadly, sometimes not even official resources are free of exploitation due to various vulnerabilities, as was the case when 50,000 Minecraft accounts were infected due to skins injected with malware capable of reformatting hard drives and deleting backups plus system programs, offered as a download on the game’s website.
Since it's usually kids (based on 2021 stats) who play Minecraft, they probably do so on shared family computers and home networks, hence the resulting damage can spill over to their parents. What’s worse, instead of an infostealer, a computer could get infected with ransomware, but that is more of a concern for gaming companies, who are targeted for monetary reasons.
Did you know?
Ransomware is a threat shared by people and businesses alike. In the world of gaming, a famous example is the 2023 Rhysida ransomware attack on Insomniac Games, the developer behind games such as Spider-Man and the Ratchet and Clank series. As a result of the attack, terabytes of data on both their past projects, as well as net-new, have been leaked.
Nothing is true; everything is permitted
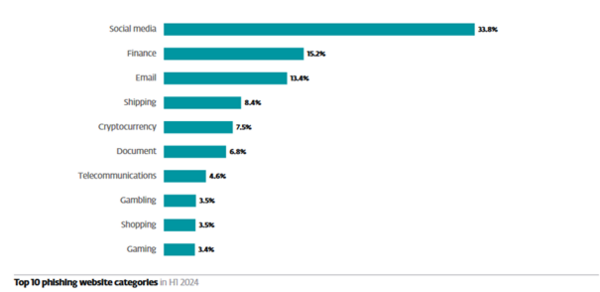
Apart from infostealers, phishing is also trendy in gaming circles. As pictured below, gaming placed No. 10 in the top phishing website category by ESET Research.
Source: ESET Threat Report H1 2024
To paint a picture of how this happens, consider when a gamer is playing an online MMO like World of Warcraft or a game with virtual currency such as Fortnite.
Character skins and various XP boosts might require you to purchase them with said virtual currency. In WoW’s case, for example, there’s the WoW token. You either purchase one with in-game gold for gametime or Battle.net balance (enabling real currency purchases), or do the opposite and purchase one for an influx of in-game gold with real money. Imagine it as a foreign exchange of sorts.
Similarly, in Fortnite, V-Bucks are used to purchase outfits, emotes, and Battle Passes. All these are rather tempting for various reasons, especially when you want to stand out among an online crowd.
Kids, teenagers, and even adults don’t know better sometimes. Via the chat functions in these games (unless disabled or if the account has a parental lock), gamers can be tempted by fellow players to visit certain websites to receive either currency for free! Just insert your login details and you’ll immediately receive an influx of your desired virtual cash/token. Or, more likely, your credentials and account will get stolen, since now you’ve been successfully phished by a cybercriminal.
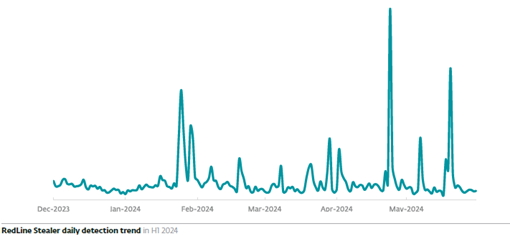
Infostealer detections
ESET telemetry continues to detect threats like RedLine Stealer and Lumma Stealer, with the former achieving localized detection peaks coming mostly from states such as Germany, Spain, and Japan.
Source: ESET Threat Report H1 2024
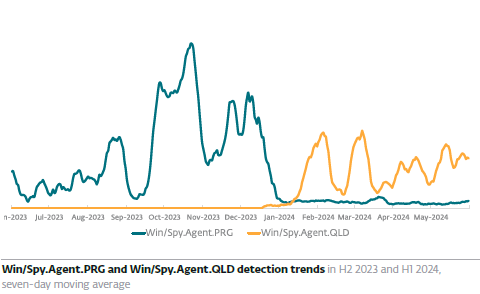
On the other hand, Lumma switched its malware to a new variant, leading to a growing trend in its detections as Win/Spy.Agent.QLD.
Source: ESET Threat Report H1 2024
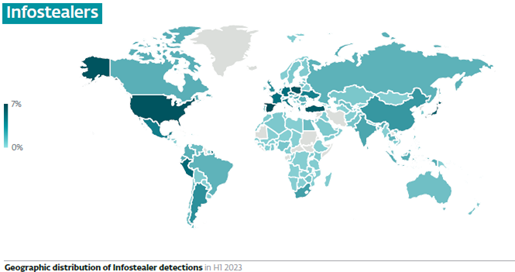
Both infostealers have been detected in payloads of files masking themselves as cheating tools or video game cracks (game executables bypassing copy protection). All in all, infostealers have seen a slight rise compared to the previous period (4% increase) globally.
Global infostealer detections. This also includes non-gaming-related ones.
(Source: ESET Threat Report H1 2024)
ESET has also detected Epsilon Stealer (as JS/PSW.Agent trojan variants .CH and .CI). It was recently present in a popular mod of Slay the Spire, pushed through the Steam update system, after having breached the developer accounts on Steam and Discord. Once installed, Epsilon looks to exfiltrate cookies, saved passwords, and credit card details from web browsers, plus login info for Steam, Windows, and other accounts.
Stay awhile and listen
To protect against infostealers and other malicious threats, your best bet is to raise your protection with strong next-gen security software like ESET Home Security, and thanks to ESET telemetry and ESET LiveSense security layers, it can assure a strong safety net in case a modpack gets infected or If someone downloads an infected executable that had already been caught by one of our global sensors.
The same software also offers anti-phishing protection and secure browsing to block suspicious websites or emails, and to guarantee a safe browsing experience while socializing online.
As for account security, use diverse passwords (we recommend using the ESET Password Generator to ensure their strength), store your credentials in password managers (instead of browsers), and use app or biometrics-based multi-factor authentication instead of SMS to add another layer to your account’s security, keeping threat actors at bay.