ESET collaborated with the Federal Police of Brazil, providing technical analysis and information gathered from ESET telemetry and tracked command and control servers.
ESET has a long history of cooperation with agencies such as Europol and Interpol, achieving excellent results, particularly in botnet tracking, an approach described by ESET senior malware researcher Jakub Souček at the ESET Technology Conference 2024, an annual ESET conference focusing on the best in our security solutions and research.
The successful mitigation of the Grandoreiro banking trojan is one such case. In a joint effort between ESET, Interpol, Europol, and the Federal Police of Brazil, several arrests were made in January 2024 concerning the Grandoreiro campaign in Brazil, causing a serious blow to the botnet’s operation.
“I believe you’ll agree with me that arresting cybercriminals is the best way to put an end to their malevolent career and to make the world safer, one botnet take-down at a time. While only law enforcement can do that, we, as the private sector, are often crucial to their success,” Souček said.
What is Grandoreiro?
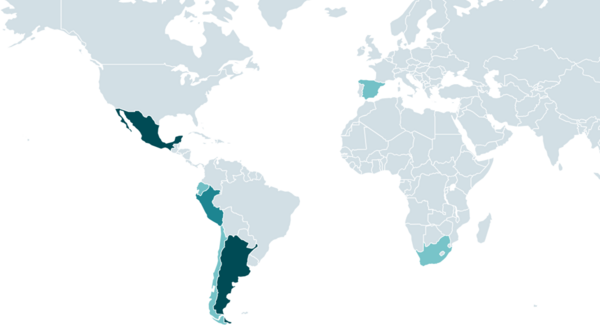
Grandoreiro is one of many Latin American banking trojans that has been active since at least 2017 and ESET researchers have been closely tracking it ever since. It has been spreading widely via phishing emails containing Grandoreiro as an attachment or links pointing to it. Most of its targets have been in Brazil, Mexico, and Spain, though in 2024 Grandoreiro heavily targeted Argentina.
The Grandoreiro malware knows when a victim opens the webpage of a targeted bank because it periodically monitors the foreground window patiently waiting for a string of characters matching its hardcoded list of bank-related strings to appear. When it happens, the malware initiates communication with a command & control (C&C) server and notifies a Grandoreiro operator who can now interact manually with the compromised machine to steal a victim’s money.
To hide the C&C servers, Grandoreiro uses a domain generation algorithm (DGA). In short, this means that, instead of providing actual domains, a generation algorithm yields a random C&C server domain, and it is up to the threat actor to make sure such domain exists and resolves to an IP address belonging to a C&C server.
When communication between the operator and the victim’s device is established, Grandoreiro allows the operator to block the victim’s screen and display fake pop-ups resembling a banking account login request. These fake pop-ups can capture the text typed into them. Should the bank require two-factor authentication, the operator can display another pop-up tricking the user into providing the verification code. After that, an attacker has full access to the victim’s account.
Additionally, the malware also enables:
- blocking the screen of the victim
- keystroke logging
- simulating mouse and keyboard activity
- sharing the victim’s screen
- displaying fake pop-up windows
How ESET discovered Grandoreiro
ESET solutions have been reliably recognizing Grandoreiro thanks to the ESET DNA Detections feature of ESET Endpoint Security. It performs a deep analysis of the code, extracts “genes” responsible for its behavior, and constructs DNA Detections, which are used to assess potentially suspect code, whether found on the disk or running in memory.
While malicious code can be modified or obfuscated by attackers, the behavior of objects cannot be changed so easily. DNA Detections can identify specific known malware samples, new variants of a known malware family, or even previously unseen or unknown malware that contains genes that indicate malicious behavior.
In addition, ESET Botnet Protection also comes in handy as it is designed to discover malware by analyzing its network communication protocols, for example when malware tries to connect the targeted computer to a botnet network. In fact, ESET has been providing protection against Grandoreiro through this system since 2017 by carefully analyzing every incoming new Grandoreiro malware sample.
ESET Endpoint Security is complemented by ESET LiveGrid, a global reputation system tirelessly absorbing data from millions of endpoints around the globe to constantly update threat intelligence. AI and human expertise process this data, allowing ESET solutions to quickly respond even to never-before-seen threats.
Worried about Latin American banking trojans such as Grandoreiro? Here are a few tips:
Don’t get hooked by phishing attacks – Malware often enters the victim’s device through phishing. Stay vigilant when opening emails, clicking on links, or browsing websites.
Use multi-layered security solutions focusing on prevention – Robust cybersecurity solutions including Anti-Phishing, Banking & Payment Protection, Secure Browser and Botnet Protection can stop malware from being deployed in your device.
Use multi-factor authentication (MFA) – This can often stop attackers despite the victim’s account details being compromised.
Scan your device – If you get unexpected pop-up windows or anything seems off, run a malware scan and follow standard remediation steps.
Verify – If you sense suspicious activity related to banking operations, verify it with your bank.
Studying malware
ESET not only protects but also studies discovered malware to improve ESET detection engine capabilities even further. Moreover, ESET researchers try to cluster affiliates to better understand the business side of investigated malware and associate those with other malicious activity.
Studying malware is part of the ESET prevention-first approach built around multilayered prevention strategies addressing all aspects of the computing environment such as minimizing attack surface, reducing the complexity of IT and cybersecurity management, and cyber hygiene. This approach vastly increases cybersecurity solutions’ capabilities to deflect an attack before it does any harm securing business continuity without any disruptions.
To learn more about Grandoreiro, ESET researchers processed every new malware sample and extracted its full DGA configuration, botnet ID, and a list of targets. They also similarly monitored Grandoreiro’s custom downloaders.
By emulating Grandoreiro’s network protocol, ESET researchers learned of a fatal flaw – every time anyone connects to the C&C server, it replies with the list of the login strings of other connected devices at that time providing vital information about victims. Furthermore, thanks to identifying all existing DGA configurations, they were aware of all existing C&C servers.
Since then, ESET researchers have been periodically communicating with every possible C&C server to see which bank triggers the C&C connection, how long a victim’s machine is running, when the connected sample is compiled, and what operating systems victims use. They also gathered limited information about the countries the victims come from. But, most importantly, they collected statistics about the number of connected victims to help law enforcement “look the right way”.
“This allowed us to not only rely on our telemetry but to see the actual reality, something very rare unless you seize the server,” Souček said.
ESET shares threat knowledge with clients using ESET Threat Intelligence, and with law enforcement authorities, so they can ultimately identify and arrest perpetrators.
The fruits of ESET labor
Grandoreiro's case shows the importance of multilayered prevention-first protection that prevents malware from being deployed in protected devices and demonstrates the power of collaborative effort in making the cyber world safer.
After sharing the data about C&C servers with ESET partners in the private and government sectors, law enforcement authorities not only disrupted Grandoreiro but, during their analysis of the seized materials, police were able to link the Grandoreiro perpetrators to old cases they investigated, related to other criminal activity. They also discovered that one of the arrested suspects had very close relations with Mekotio, another infamous LATAM banking trojan.
“Law enforcement has limited resources, so it benefits greatly from such data, as it helps them look the right way and utilize their limited manpower as efficiently as possible,” Souček said.
