At the annual internal ESET Technology Conference 2024 (ETeC), a series of high-powered workshops, seminars, hackathons, and presentations occurred.
ESET experts Gabriel Balla (product manager for Enterprise Solutions and Services), James Rodewald (security monitoring analyst), and Michal Hajovsky (global sales lead) provided a sneak peek into ESET MDR – its evolution, backend systems, delivery, as well as success stories demonstrating its ultimate value for businesses of all sizes.
The road to success with ESET MDR
During the initial session with Gabriel Balla and James Rodewald, some of the most influential aspects of ESET MDR on business security, both past successes and future prospects, were discussed.
Balla began by describing a familiar situation many generalist IT admins face – an overabundance of tasks that heavily impact the overall quality of an organization’s security, as admins have to contend with matters such as user support, various device maintenance, monitoring, and more – daily at that.
This is especially burdensome for small and medium-sized businesses (SMBs), which might lack:
- Budget: SMBs have fewer resources to spend on high-level security and, as specialists are costly and not in abundance, they face tough competition from competitors with larger wallets.
- Time: An average EDR/XDR solution might generate up to 160,000 detections for an SMB with just 250 seats. This requires lots of dedicated time and understanding to sort through, possibly resulting in alert fatigue.
- Knowledge: Identifying threats requires professional skills while understanding the newest threats targeting businesses is another heavy task altogether.
While enterprises might not see these points as untenable, they have their specific issues, such as having a larger attack surface with multiple weak spots. Moreover, an enterprise requires finely-tuned preventive security, since the larger a business is, the more likely it is to face issues related to spotty coverage (missed devices) or compliance (country-specific regulations).
In fact, Rodewald later described a situation in which someone had purchased a security service but forgot to deploy it – which might sound comical, if not for its potential to end up causing a costly incident.
How to demonstrate the value of MDR within 30 days
So, why would an SMB want an MDR service? Equally, why would an enterprise need something other than its own Security Operation Center (SOC)?
Hajovsky easily answered these questions: “As much as 82% of ransomware attacks target SMBs. Businesses can break even with endpoint on, as threat actors can get in without using malware, just by abusing RDP or MS SQL…so the initial behavior is, therefore, crucial to monitor for,” he said. Time to detect and respond is crucial. On average, the detection of malicious behavior in business systems takes around 277 days, without any EDR/XDR solution.
For an enterprise SOC, it should take around 16 hours, which is a lot better, but with MDR, this can all be done in less than 30 minutes, due to the way an MDR service is set up. Hajovsky also highlighted that many businesses don’t have the time to dedicate their teams solely to security management. Likewise, with the need for constant education on novel threats, more expertise for threat hunting and incident remediation is required – which is often missing due to skills shortages.
However, ESET MDR, for example, is manned by top experts working with powerful in-house SOAR/SIEM tools ingesting data from multiple points, using a dash of AI-native power, ESET research, and actionable threat intelligence to empower fast proactive threat detection and threat hunting. Additional value can also be found in satisfying compliance and insurance requirements – often asking for EDR/XDR for lower premiums or as a condition.
Don’t believe it? Try it. ESET offers an ESET MDR Trial that can demonstrate its power shortly after deployment – so if the prospects are that you’re not ready to buy, you are most probably ready to try :)
ESET MDR success stories
Rodewald dedicated his side of the ESET MDR tale to describing successes – in detail.
In one success story, ESET MDR operators noticed that odd-looking user accounts had started to appear, each added to local administrators. This was being done by a mesh agent (an open-source RMM tool for network management), which is not usually malicious. However, the mesh agent had been installed in a c2Update folder (sounding suspiciously like a C&C server) by notepad.exe running from ProgramData – signaling malicious activity.
When a user account started to perform more actions, such as trying to create a reverse shell, or dropping an EXE (doing a CVE in Veeam software to dump backups) immediately detected and deleted by ESET, the intent became clear: “I suspect that this was likely the beginning of a ransomware or extortionware attack, since we have seen mesh agents used in the US to deploy ransomware,” said Rodewald.
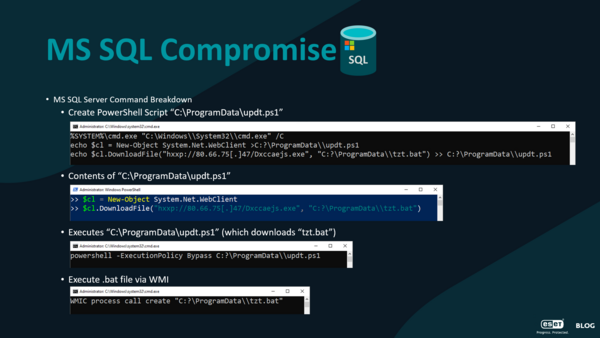
In another success story, ESET analysts saw EsetIpBlacklist detected on a port that was actively used by an sqlserver.exe process, exposed to the internet. The same process was compromised by an outside connection, logging into MS SQL, making themselves into an admin, and starting to execute commands on the OS. The MDR team acted quickly. “The best course of action was to isolate the device – by cutting them off, they weren’t able to execute new commands,” elaborated Rodewald.
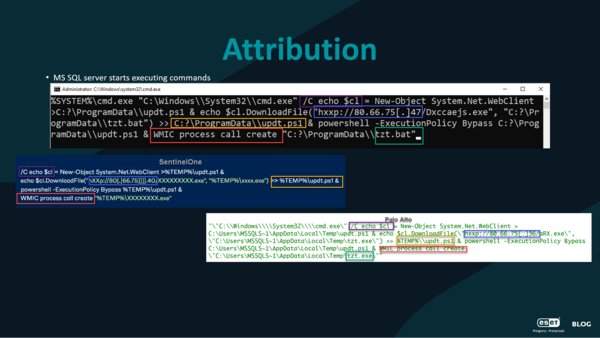
Upon further analysis, the team discovered that the MS SQL server command tried to create a PowerShell script named updt.ps1 (downloading a file saved as tzt.bat) and execute it with WMI. “This breaks the process tree a little bit, so without an EDR solution capable of connecting it back together, it wouldn’t look like MS SQL did anything.”
After additional research, the team was able to attribute the latter attack to a case of Mallox Ransomware. “We stopped the attack before it was able to drop an EXE payload just in its initial stages as it was exploring if it could get the .bat file to run. This means that ESET MDR was able to prevent ransomware for a customer, that is a huge success as I see it,” Rodewald concluded.
Prevention first with ESET MDR
According to ESET telemetry, ransomware attacks rose by 32% in H1 2024, compared to the previous semester. This comes in tandem with large-scale compromises of small and large businesses and critical infrastructure (such as hospitals), highlighting a growing problem.
However, sophisticated threats, such as ransomware, are exactly what services like ESET MDR thrive on. They fulfill the notions of a prevention-first security approach by stealthily working in the background to let businesses keep ahead of threats without disrupting their processes.
The main takeaway, as pointed out by Gabriel Balla, should be security success without worry, free from constant notifications about detection or remediation efforts. That is the way of ESET MDR, so let ESET take care of you, and live a life full of green checkmarks indicating that everything is secure in your world.