Essential security can take care of most threats – but for businesses with larger networks, it might be time to extend the security envelope.
We’ve written before about how multilayered security is key to protection success. Each layer represents a dimension of protection, tackling specific threats or attack vectors.
The best security solution should tackle all of this behind the scenes, only requiring human attention during setup, audits, or incidents. Security should be comprehensive, yes, but not too complicated, worsening the protective power of security operations.
To learn how complicated security tools can impact a business's cybersecurity protection, read our blog on alert fatigue-induced burnout.
Moreover, the larger such an operation is, the harder it is to cover. Thankfully, some measures can alleviate such issues easily – such as automatic extended protection.
What do we mean by extended protection?
Let’s start from the bottom – the core of a security operation: endpoint protection, covering computers, mobile devices, and servers. Such points of convergence between users and digital networks are prime targets for threat actors, necessitating constant safeguarding.
Baseline endpoint protection should serve the smallest businesses, but larger ones might find that this is just not enough to cover their use of various cloud and mail apps, authentication, or a potential cyber insurance ask in the form of advanced encryption. Furthermore, larger businesses also require advanced threat defenses, somewhere beyond stand-alone endpoint security. This could be a protective sandbox set up to catch any incoming malicious samples, such as zero-day threats, before they hit the endpoint itself, or vulnerability and patch management to take care of exploitable gaps before they become an issue.
At ESET, we call all this extended protection – as it extends beyond endpoint security, adding additional protective layers, extending prevention efforts.
Why should a business want extended security tech?
The easy answer to why a business should seek extended protection is that their involvement in commerce is enough of an incentive for threat actors to have them in their sights. Based on various reports, cracking the security of SMBs and larger businesses is the most likely goal rather than well-defended enterprises (a business with fewer than 100 employees could face 350% more attacks than enterprises).
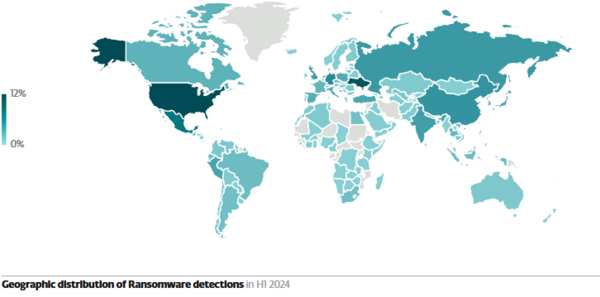
Ransomware, a threat likely faced by every business entity, has seen a 32% rise in H1 2024 compared to H2 2023, based on ESET threat telemetry, with most detections present in the US, Mexico, the UK, and Germany.
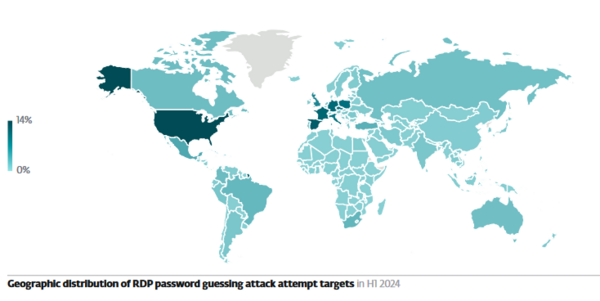
Moreover, similar trends are seen in remote desktop protocol (RDP) password-guessing attempts (a rise of 33%), with numerous detections in additional countries like the US, Brazil, Spain, France, Italy, Germany, Czechia, and Poland. Shockingly, despite numerous return-to-office mandates, the now common use of RDP for remote employees in hybrid work has seen the incidence of attacks continue to rise.
ESET telemetry also highlights the diversity of popular vulnerable external network intrusion vectors. While password guessing is highly represented statistically, it is followed by Log4j, Struts, and various other vulnerabilities, targeting RDP or VPN apps.
Most of the represented intrusion vectors concern key business apps that are used globally. Additionally, a majority of the represented Common Vulnerabilities and Exposures (CVEs) have patches. Despite this, they are still being actively exploited – meaning that businesses are not patching their tools, creating major opportunities for threat actors.
How to ensure extended protection
To ward off threat actors abusing a diversity of vectors, let’s tackle extended network needs step by step:
Advanced threat defense
To give additional protection against new and unknown threats, advanced defense is a good idea. In this case, it is done by adding a cloud filter on top of endpoint security, creating a sandboxed environment, such as with ESET LiveGuard Advanced, that can perform in-depth behavioral analyses to prevent targeted attacks, such as ransomware or attacks via the supply chain. This effectively places defenses outside a corporate network, preventing threats from executing inside.
Cloud and mail
Think of the sort of collaborative cloud and mail apps you use (Teams, OneDrive, Gmail, SharePoint), and consider how they enhance a network and connect it to points outside the premises of your organization – leading to extended collaboration opportunities.
As explained by ESET Security Writer Roman Cuprik, large cloud platforms have seen rapid growth, accounting for as much as 280 million users – inviting malicious actors to abuse them for gain. For example, GIFShell enabled threat actors to misuse MS Teams for phishing, executing commands to steal data using GIFs.
Therefore, protecting the cloud and mail through solutions such as ESET Cloud Office Security and ESET Mail Security is an easy way to prevent abuse, as they actively scans all files at all points of their life in the cloud – stopping spam, malware, phishing, and other threats early.
Authentication
It was previously mentioned that password-guessing attacks are quite common. Passwords themselves are often not enough to ensure account security, either because they have been leaked as part of a security breach or because of their simplicity, becoming easily brute-forced.
Thus, secure authentication adds a layer on top, preventing password misuse from letting attackers gain access to user accounts. This is very useful also in the case of RDP and VPN security, as those are also easily compromised through credential misuse. With authentication, though, security is ensured by the provision of one-time-use, time-limited codes or tokens, as attackers would need access to this factor to verify their access attempt.
Encryption
A basic compliance and cyber-insurance ask is encryption. Most often associated with data at rest (storage), encryption prevents physical exploitation of endpoint devices in case a computer, for example, is stolen. Encryption also minimizes risk stemming from data breaches, as specific solutions such as ESET Full Disk Encryption make sure that data are protected at all times.
Vulnerability and patch management (V&PM)
Known vulnerabilities (CVEs) present a major exploitable attack vector, open to abuse by malicious actors. CVEs can be present both in apps and OSs, which is why security updates exist to tackle any vulnerability gaps.
However, some businesses forget or don’t do this, leading to data breaches due to negligence. This can be followed by denied insurance claims and compliance-induced fines for not dealing with known security gaps. To prevent such cases comprehensively, think about obtaining a V&PM solution with automatic updates that satisfies this need in the background.
(Ex)tending your security
Extended security doesn’t mean extending security resources. Most of the previous solutions don’t require manual adjustments apart from initial setup, as the greatest thing about automation these days is its quiet but significant impact.
Think of it as a cardboard box – while the foil and soft particles (multilayered security) inside protect the integrity of your purchased product (endpoint), extended protection plugs any voids (vulnerabilities), tapes over the edges (encryption) and puts a cargo truck between the box and the outside world (advanced threat defense) to protect it from direct damage. As for authentication, every delivery must be signed for. :)
For more information on how multilayered endpoint security serves as a powerful core of business protection, read our blog posts on Fileless malware and UEFI bootkits.